Configuration of the IGEL Agent for Imprivata on IGEL OS
Before You Begin
Review the Supported Features and Workflows: IGEL Agent for Imprivata (IAFI) Feature Comparison Matrix
Review the IAFI Workflow Configuration Options
Review the IAFI Terminology Glossary
Requirements
Review the Imprivata Requirements
Review the IAFI - IGEL System Requirements
Add-on license that can be acquired via the request form at IGEL Agent for Imprivata
Configuring Basic Settings
In the profile configurator, go to Apps > IGEL Agent for Imprivata.
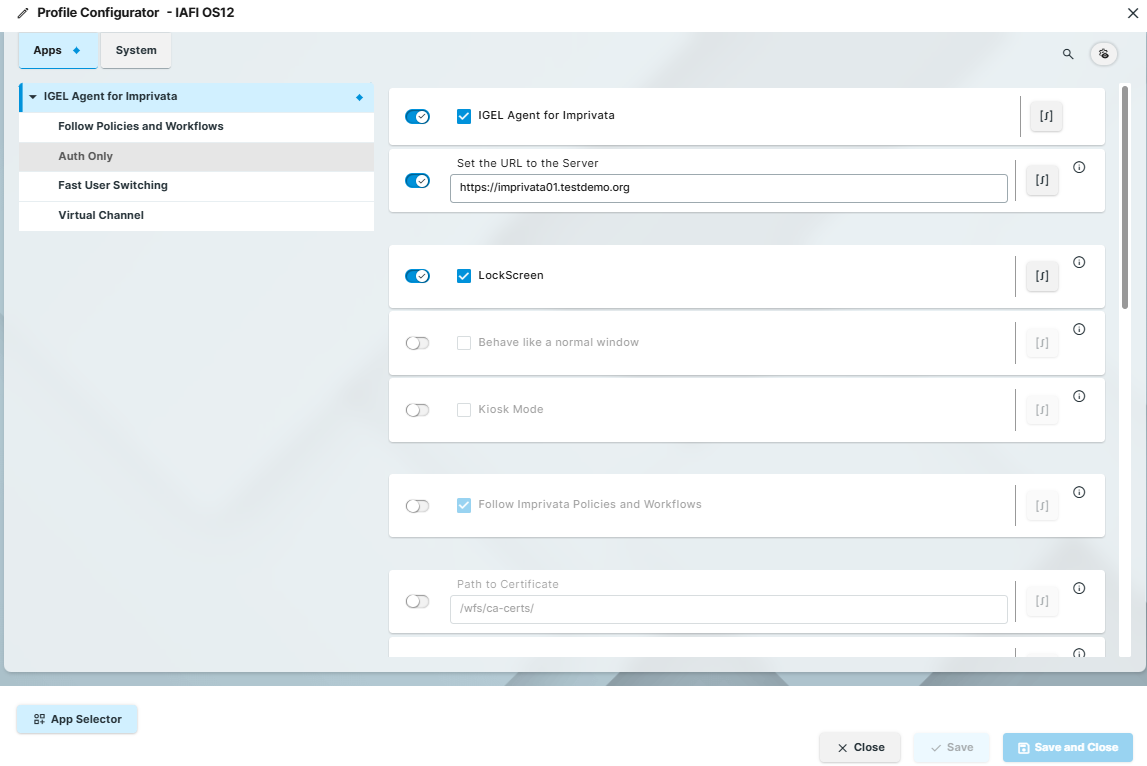
Edit the settings according to your needs. The parameters are described below according to how they appear in the profile configurator.
Some settings are only in the App registry and may be moved into the profile configurator in future releases.
IGEL Imprivata Agent
☑ The IGEL Agent for Imprivata is enabled.
☐ The IGEL Agent for Imprivata is disabled. (Default)
Registry | Value |
|---|---|
| False (default), True |
Set the URL to the server
Type in the URL address of the Imprivata Appliance. This needs to be the FQDN of at least one appliance.
For appliance failover with multiple appliances, separate the URL’s using a semicolon “ ; “ and no spaces.
Example: https://imprivata01.demolab.org;https://imprivata02.demolab.org;https://imprivata03.demolab.org
Related IAFI Configuration settings:
Path to Certificate
Skip Certificate Verification
Connection timeout
Registry | Value |
|---|---|
| Blank (default) |
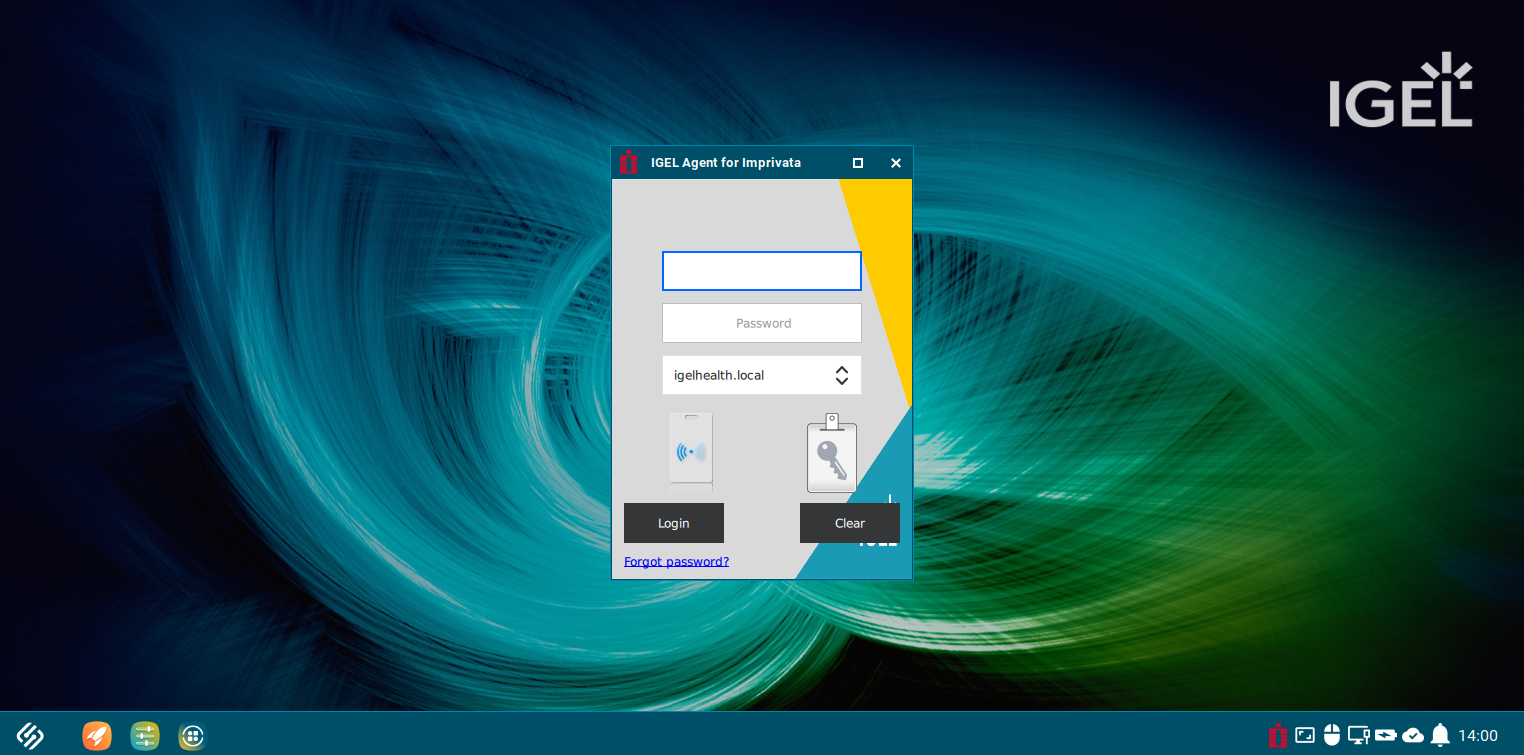
LockScreen
☑ When enabled, the agent will be in a full lock screen, similar to Appliance Mode in OS 11 with the Imprivata PIE agent. Only the Imprivata agent authentication dialogs and a background image are displayed. The IGEL desktop is not accessible.
☐ The Lockscreen is disabled. (Default)
In the default setting, the agent will start in a compact mode login in the bottom right corner of the screen with a portion of the IGEL desktop accessible.

IAFI default login screen setting (Compact Mode)

IAFI Lockscreen enabled (with the default background image)
Registry | Value |
|---|---|
| False (default), True |
Related IAFI Profile Configuration Lockscreen settings:
Choose the Background Image
Show Computername on Lockscreen (upper right corner of the screen)
Lockscreen Shortcut
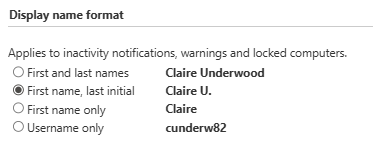
Show the username at the Lockscreen (Registry Only)
This is related to an Imprivata Computer Policy setting: General - Display name format
You can change the format based on the policy options.
If you don’t want to show the logged in user on the lock screen, disable this in the registry.
Registry | Value |
|---|---|
| False, True (default) |
Behave like a normal window
☑ When enabled, this setting undocks the compact login screen from the IGEL taskbar and places it in the middle of the screen.
☐ Disabled (Default)
This feature is an option primarily for the Follow Imprivata Policies and Workflows configuration that will use the IAFI Resource Chooser. However, if you want the IAFI login to be in a Windows mode (not Fullscreen), you could also use this with the Auth Only configuration.
Registry | Value |
|---|---|
| False (default), True |
IAFI compact login in Windowed Mode
Enabling the Windowed mode setting will also impact the IAFI resource chooser (Apps or Desktops).
IAFI Compact Mode Login and Resource Chooser behavior:
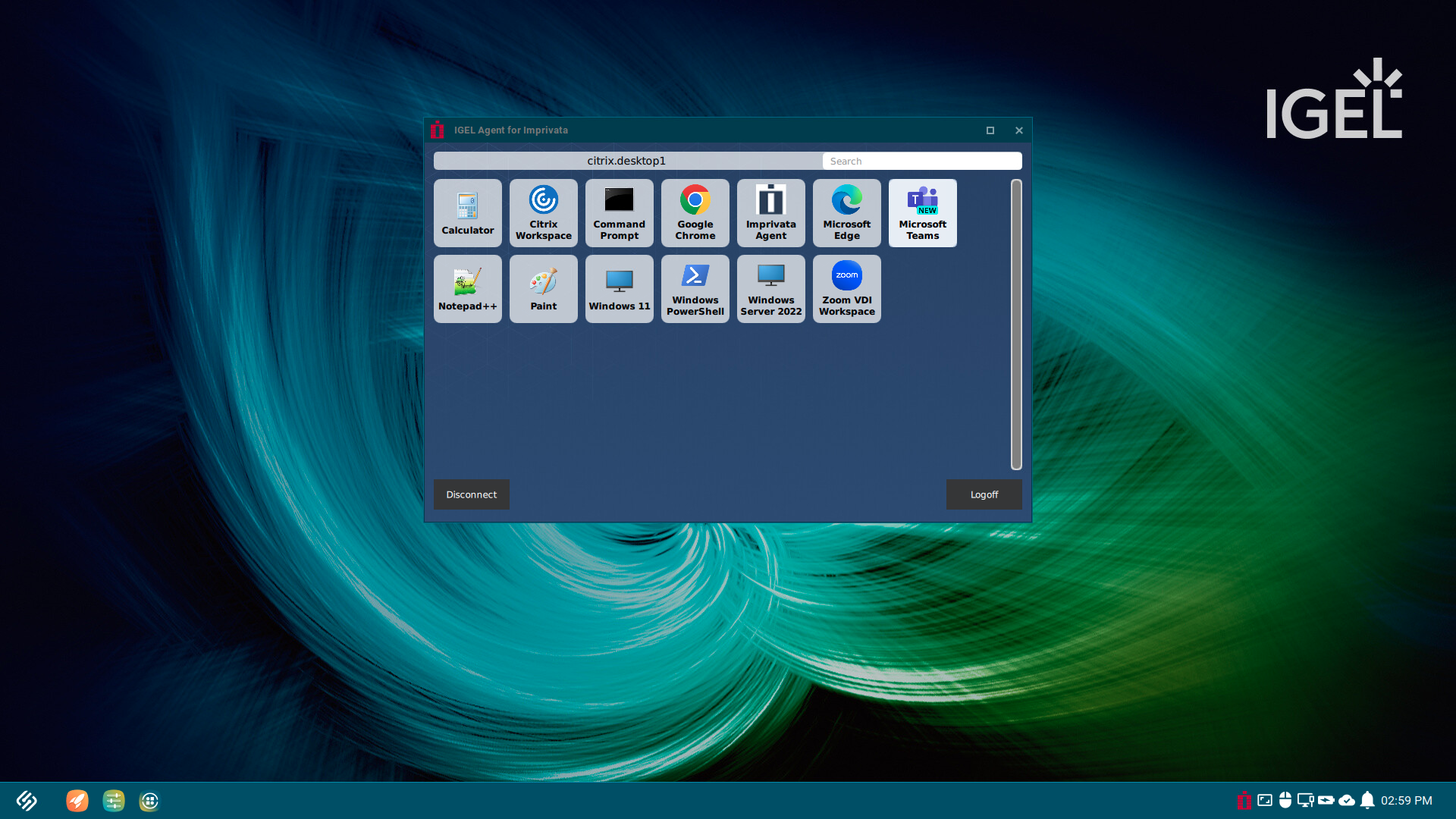
No Autolaunch of Imprivata VDA resources
By default, if the Imprivata VDA User Policy for “Automate access to applications or published desktops” does not have any resources set to autolaunch, then the IAFI resource chooser will show in the middle of the screen after a user logs into the agent.
The user will have to manually select the resources to launch.
The chooser will be available for other resources to launch if necessary.
The chooser shows the logged in user, a search option to filter on resource names and a scroll bar on the right side.
Autolaunch of Imprivata VDA resources
If the Imprivata VDA policy is set to autolaunch any resources, then by default, the IAFI resource chooser will NOT appear after the user logs in.
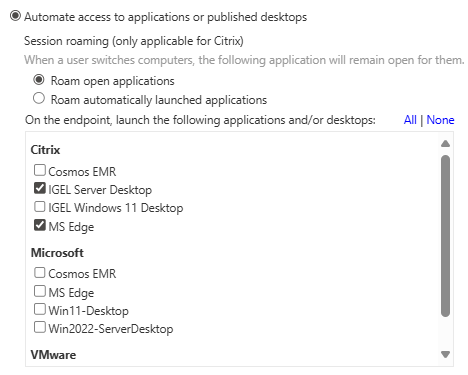
There is an IAFI registry setting that can change this behavior.
Changing the IAFI registry setting to keep the resource chooser available for Autolaunch workflows:
Enabling this will keep the IAFI resource chooser available if the Imprivata VDA User Policy “Automate access to applications or published desktop” dictates autolaunching of resources (apps or desktops).
After a resource is autolaunched, the user can go to the IAFI chooser to select other resources (apps or desktops) to manually launch.
Registry | Value |
|---|---|
| False (default), True |
Kiosk Mode
☑ When enabled, all other IAFI workflow modes (Auth Only, Follow Policies, FUS) are disabled and those settings do not apply.
☐ Disabled (Default)
NOTE: In Kiosk Mode, the agent runs as a service to provide virtual channel support for Imprivata authentication devices. Currently, this is Proximity Readers. Future IAFI versions will also support Fingerprint readers.
Kiosk Mode supports these common Imprivata workflows:
Virtual kiosks (Imprivata Type 2 agent)
Epic Only workflows
Can be used for Citrix, Horizon, Microsoft RDP, AVD, or Windows 365 Cloud PC kiosk sessions
Does not require USB redirection of supported Imprivata proximity card readers
Registry | Value |
|---|---|
| False (default), True |
Follow Imprivata Policies and Workflows
This is the default configuration mode for IAFI. Generally speaking, this mode mimics the same workflows as the Imprivata PIE agent. When enabled, the Imprivata Virtual Desktop Access User and Computer policies that are defined on the Imprivata appliance will be applied such as the automatic startup of Citrix, Horizon or RDP sessions on login.
☑ Enabled (Default)
☐ Disabled
When disabled, the agent switches to Auth Only mode and the Imprivata appliance is only used as an identity provider. No further VDA policy automation will be evaluated or executed. Instead, the credentials that are passed on from the Imprivata appliance will be securely stuffed into the session that is defined under Auth Only preconfigured session. Auth Only mode can be used for connecting to AVD, Windows 365, Citrix or Horizon sessions.
Registry | Value |
|---|---|
| False, True (default) |
Path to certificate
☑ The default is set to: /wfs/ca-certs/ and you do not have to specify the name of the certificate itself.
IAFI will look at certificates in that directory when they are deployed from the UMS server. Follow these guidelines for deploying the Imprivata appliance certificate(s) from UMS to the devices. How to Deploy the Imprivata Appliance Certificate(s) to IGEL Devices
Registry | Value |
|---|---|
| /wfs/ca-certs |
Skip certificate verification
This can be used when you don’t have the appliance certificate or the certificate chain deployed to the IGEL device. IGEL does not recommend enabling this setting for production use.
☑ When enabled, this skips appliance certificate verification and allows the agent to connect to the Imprivata appliance.
☐ Disabled (default)
Registry | Value |
|---|---|
| False (default), True |
Connection timeout
The timeout in seconds when the agent is connecting to the appliance.
The default is 20 seconds but can be adjusted to a lower or higher number. IGEL does not recommend lowering this below 3 seconds.
Related setting: Set the URL to the server
If multiple appliances are listed, after the timeout setting is reached, the agent will contact the next appliance listed.
Registry | Value |
|---|---|
| 20 |
Default entry of domain list
☑ When enabled, you can specify the name of a specific domain if more than one is configured in the Imprivata Appliance directories.
☐ Setting is blank and will use the domains provided by the appliance in alphabetical order. (Default)
Registry | Value |
|---|---|
| Blank |
Choose the Background Image
IAFI has three options for the lockscreen background image.
Default image (Default)
Imprivata Appliance image (pulled from the Computer Policy - Customization settings)
Custom Image deployed from the UMS Server to:
/wfs/
See this KB article for more information on customizing the background image.
Registry | Value |
|---|---|
| default (Default), appliance, custom |
Hide agent window when idle
☑ When enabled, this hides the agent compact dialog after a user logs in. You can click the agent icon in the IGEL system tray to display the popup window.
☐ The agent compact dialog will be displayed in the bottom right corner after a user logs in. (Default)
Registry | Value |
|---|---|
| False (default), True |
Lockscreen Shortcut
This shortcut setting allows you to toggle the lockscreen if you need to quickly access the IGEL desktop. It is disabled by default (blank).
You can type a keyboard shortcut of your choosing. IGEL only supports two key combinations. Example shortcut keys are:
Esc
Esc, q
Alt, x
Registry | Value |
|---|---|
| Blank (default) |
Query Email from App Moniker
This is not a required setting but an option that can be used for IAFI Auth Only mode for Microsoft AVD or Windows 365 Cloud PCs. You would specify the name of the IGEL AVD app profile that is configured in the appliance “application mapping” section.
Registry | Value |
|---|---|
| Blank (default) |
Allow tap-over of running session
☑ Enabled (Default) - Another user can take over the device even when a user is still logged in. The session of the previous user will be disconnected, or the previous user will be logged off. (Default)
☐ Disabled - There is no possibility for another user to log in while a user is logged in.
Related IAFI settings
Follow Policies and Workflows > Default on how to leave a follow policies session
Auth Only > default on how to leave a AuthOnly session
Auth Only > When an endpoint is locked
Registry | Value |
|---|---|
| True (default), False |
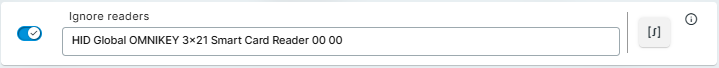
Ignore readers
This is only needed when an embedded smartcard (PCSC) reader is built into the IGEL device (ex: thin client, laptop) or an external keyboard. The agent recognizes the PCSC reader and displays it as a proximity reader on the IAFI login screen even though you can’t tap a badge.
To ignore the PCSC reader:
Enable the Ignore readers setting in the IAFI profile
on the device, open a terminal, log in as user or root.
At the command prompt, type: pcsclistreaders
The output should display the name of the PCSC reader(s) and the slot numbers
For example, the output may look like this: HID Global OMNIKEY 3x21 Smart Card Reader 00 00
Copy the output and paste it into the “Ignore readers” field
NOTE: if there are multiple PCSC readers, they will be displayed as a list. You can add both readers separated by a semicolon ( ; )
In this example, you see both a keyboard device and USB smartcard reader.
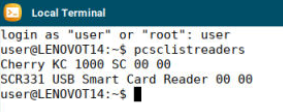
To add both of these devices to the Ignore readers field, it would look like this:
Cherry KC 1000 SC 00 00;SCR331 USB Smart Card Reader 00 00
Registry | Value |
|---|---|
| Blank (default) |
Logging Verbosity
There are three IAFI logging options to choose from:
info (default)
debug
error
See this IAFI Article for more information on enabling debug logging.
How to Enable and Export IAFI Debug Logging for Troubleshooting
Registry | Value |
|---|---|
| info (default), debug, error |
Configuring Follow Policies and Workflows
Default on how to leave a follow policies session
Defines the behavior of the IGEL Agent for Imprivata when users tap their cards to leave the session.
Possible options:
disconnect: The user is disconnected from the session. (Default)
logoff: The user is logged out of the session.
Registry | Value |
|---|---|
| disconnect (Default), logoff |
Starting with IAFI 1.3.0 and higher, there is a new feature that supports the Imprivata VDA Computer Policy setting to keep a session active when the endpoint is locked as shown in this example.
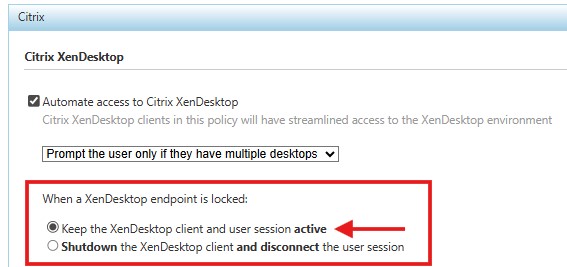
IMPORTANT: In Follow Policies Mode, IAFI 1.3.0 and higher will honor this setting if it is enabled.
NetScaler COOKIEINSERT
Supports the Citrix NetScaler COOKIEINSERT Session Persistence method for Load Balanced sessions.
Session persistence maintains the connection between an endpoint and the Citrix Storefront after load balancing is performed. A common way to maintain session persistence is to use the endpoint source IP address. However, customers who use Network Address Translation (NAT) in front of a NetScaler load balancer cannot use this persistence method, because endpoints appear to have the same IP address at the load balancer.
Those customers must use the NetScaler COOKIEINSERT session persistence method. This method causes the NetScaler to insert a cookie into client requests, which the NetScaler uses to track the server to which the connection belongs.
See this Imprivata documentation article for reference.
☑ enabled - Enter the COOKIEINSERT value from the NetScaler. Example: IGELOS12
☐ disabled (default)
Make sure that the cookie names are the same on the NetScaler and the IGEL endpoints.
Registry | Value |
|---|---|
| Blank (default) |
Hide apps on the Citrix Chooser
☑ enabled (default)
☐ disabled
This setting filters out Citrix Apps in the IAFI Resource Chooser. Only Citrix desktops will be shown.
When disabled, the IAFI Resource Chooser will display Desktops and Apps that a user is entitled to.
NOTE: This setting is similar to how the Imprivata PIE agent Chooser works with XenDesktop VDA. Only Citrix desktop icons will appear if the user has multiple resources.
Registry | Value |
|---|---|
| True (default), False |
Hide apps on the Horizon Chooser
☑ enabled (default)
☐ disabled
This setting filters out Horizon Apps in the IAFI Resource Chooser. Only Horizon desktops will be shown.
When disabled, the IAFI Resource Chooser will display Horizon Desktops and Apps that a user is entitled to.
NOTE: This setting is similar to how the Imprivata PIE agent Chooser works with Omnissa Horizon VDA. Only Horizon desktop icons will appear if the user has multiple resources.
Registry | Value |
|---|---|
| True (default), False |
Launch a sole Horizon Desktop without prompting
☑ enabled (default)
☐ disabled
For users that only have a single Horizon desktop entitlement, IAFI will launch that resource automatically when they log in. No IAFI resource chooser will appear.
NOTE: This setting is similar to how the Imprivata PIE agent works with Horizon VDA for users with just a single desktop.
Registry | Value |
|---|---|
| True (default), False |
Preselect the Citrix resource if there are multiple
☐ enabled
☑ disabled (default)
Enter the name of the Citrix resource that should be started. Examples: "Calculator", "Notepad", “Windows 11”.
If this field is blank, and there are multiple Citrix resources, the IAFI Resource Chooser is shown to the user.
This is setting that can “bypass” the VDA Policy settings and automatically start a specific resource if required. A good use case is for a “Location Based Override” where in that specific area, you want to always launch a specific resource regardless of the VDA policy settings.
Registry | Value |
|---|---|
| Blank (default) |
Preselect the Horizon resource if there are multiple
☐ enabled
☑ disabled (default)
Enter the name of the Horizon resource that should be started. Examples: "Calculator", "Notepad", “Windows 11”.
If this field is blank, and there are multiple Horizon resources, the IAFI Resource Chooser is shown to the user.
This is setting that can “bypass” the VDA Policy settings and automatically start a specific resource if required. A good use case is for a “Location Based Override” where in that specific area, you want to always launch a specific resource regardless of the VDA policy settings.
Registry | Value |
|---|---|
| Blank (default) |
Preselect the Microsoft resource if there are multiple
IMPORTANT: This setting is not currently supported for Microsoft resources.
In Follow Policies and Workflows mode, IAFI only supports the Imprivata VDA policy for Microsoft Remote Desktop Services - Remote PC as seen below in the Imprivata Global VDA, Computer and User Policy settings.
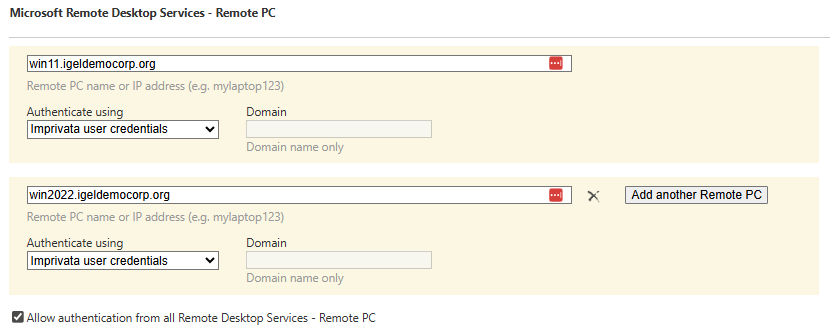
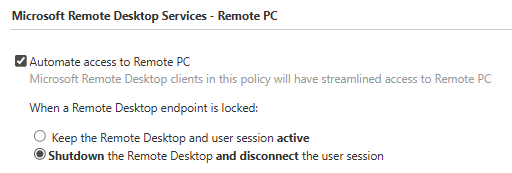
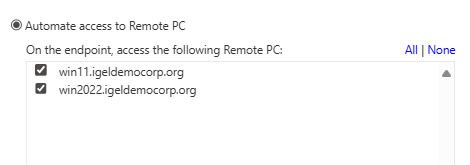
IMPORTANT:
If a user policy has more than one Remote PC enabled, IAFI will autolaunch the first one listed.
In the example above, the first resource is win11.igeldemocorp.org
☐ enabled
☑ disabled (default)
Registry | Value |
|---|---|
| Blank (default) |
Configuring Auth Only
default on how to leave a AuthOnly session
Defines the behavior of the IGEL Agent for Imprivata when users tap their cards to leave the session.
Possible options:
disconnect: The user is disconnected from the session.
logoff: The user is logged out of the session. (Default)
Registry | Value |
|---|---|
| logoff (default), disconnect |
When an endpoint is locked
Starting with IAFI 1.3.0 and higher, there is a new feature for Auth Only mode to keep a session active (vs. disconnected or logged off) when the endpoint is locked. When enabled, this keeps the user session active if the endpoint is locked via Badge Tap, Hotkey or Walkaway Security.
IMPORTANT: The IAFI Full Lockscreen should be enabled when using this setting in order to protect what is in use on the remote session (ex: virtual desktop with financial information or a patient record that requires privacy protection).
☐ Shutdown and disconnect the session (default)
☑ Keep the session active
Registry | Value |
|---|---|
| Shutdown and disconnect the session (default), Keep the session active |
Auth Only Preconfigured Session
☐ enabled
☑ disabled (default)
This is a required setting.
IMPORTANT: Enter the name of the preconfigured session resource that is to be started when the user has logged in.
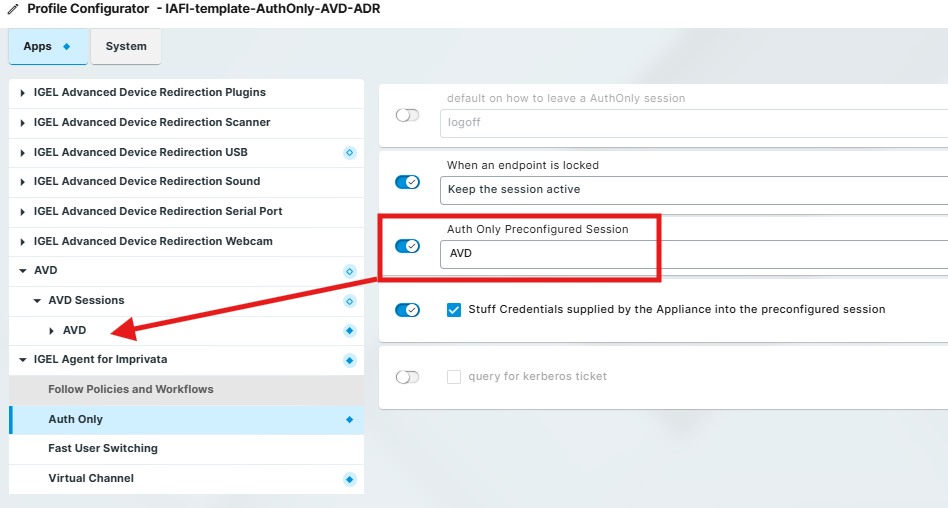
Supported Auth Only session types: AVD, Windows 365, Citrix, Horizon
Stuff credentials supplied by the appliance into the preconfigured session
☑ The credentials passed on from the Imprivata appliance will be stuffed into the session defined under Auth only preconfigured session. (Default)
☐ The user will be prompted for the credentials by the session itself.
To make the credential stuffing possible, the credentials must not be predefined for the preconfigured session. Therefore set the relevant session credential parameters to inactive so that they are not controlled by the UMS profile.
Microsoft AVD or Windows 365
For an AVD or Windows 365 session, the settings should look like this:
Apps > AVD > AVD Sessions > [session name] > Logon:
Apps > IGEL Windows 365 > Windows 365 Sessions > [session name] > Logon:
Disable the “Enable Single Sign-On” setting
Set the Username@domain or @domain and Password parameters to inactive
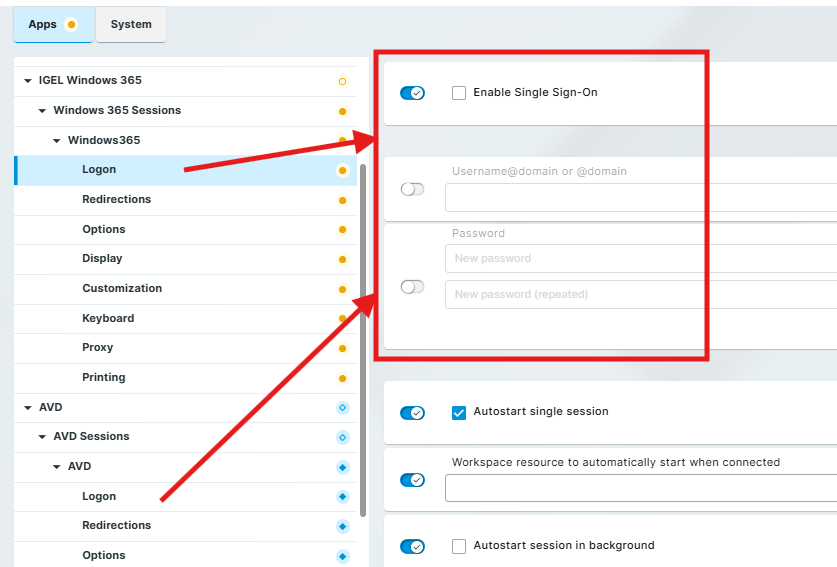
Omnissa Horizon
For a Horizon Client Auth Only session, the settings should look like this:
Apps > Horizon Client > Horizon Client Sessions > [session name] > Connection Settings:
Server URL: Enter the FQDN of the Horizon server
Lock user name: Disable or set inactive
Kiosk mode: Enable and set to ‘on’
this setting uses a noninteractive mode for the Horizon Client so the user doesn’t see a login prompt
Session type (you can only choose one session type)
Select Desktop (if connecting to a Horizon Desktop session)
OPTIONAL: Desktop name
If you want to auto launch a specific Horizon desktop, enter the name of the desktop
ex: Windows11
Select Application (if connecting to Horizon Applications)
OPTIONAL: Application
If you want to auto launch a specific Horizon application, enter the name of the app
ex: Outlook
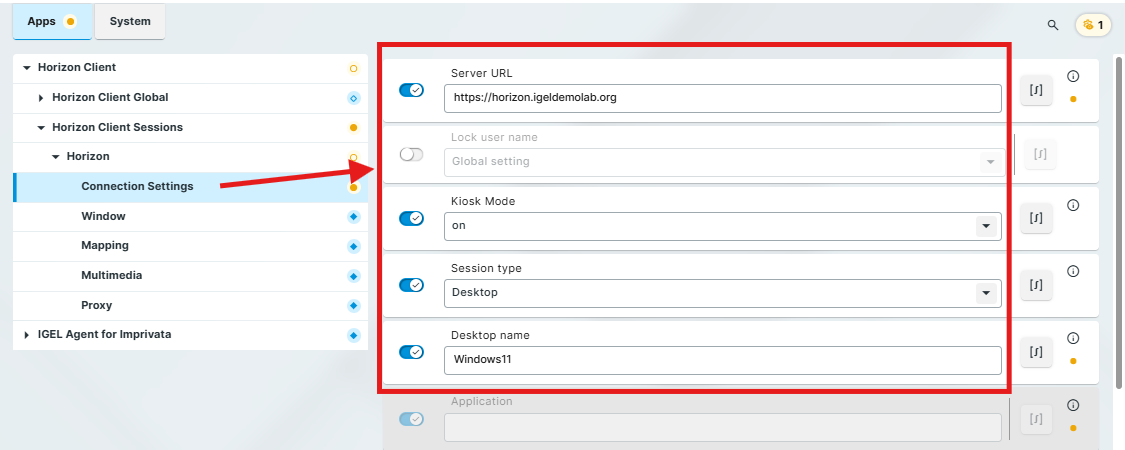
Use passthrough authentication for this session: Disable or set inactive
Save last user name: Disable or set inactive
Set inactive:
User name
User password
Domain
Autoconnect: Enable
this will automatically launch the desktop or application resource specified in the Desktop or Application name setting
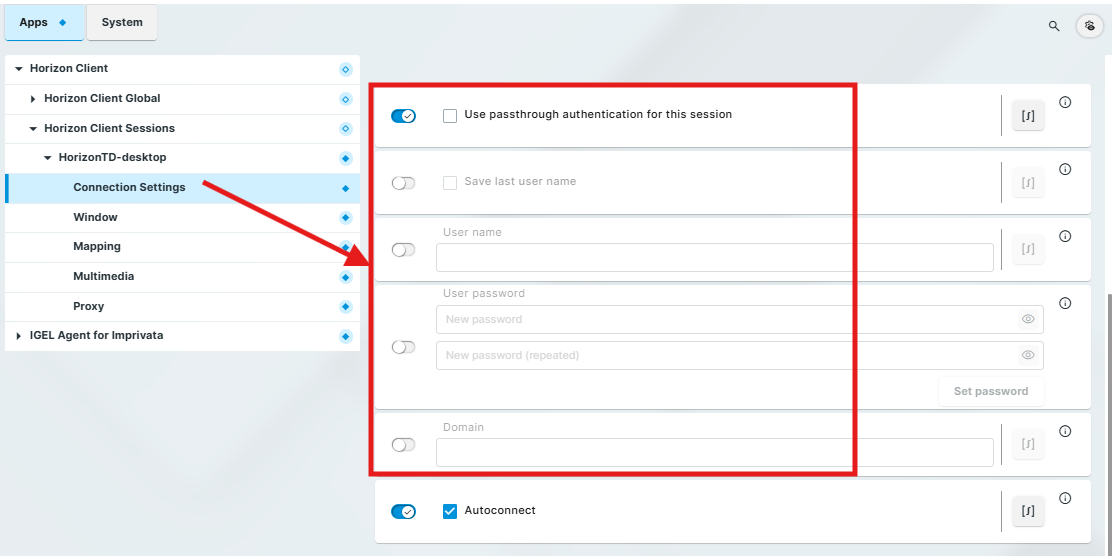
Citrix Workspace App
For a Citrix Workspace App Auth Only session, the settings under Apps > Citrix > Citrix Sessions > [session name] > Server should look like this:
Type of the session: Select Storefront
Citrix Store: Enter the FQDN URL for the Citrix Store
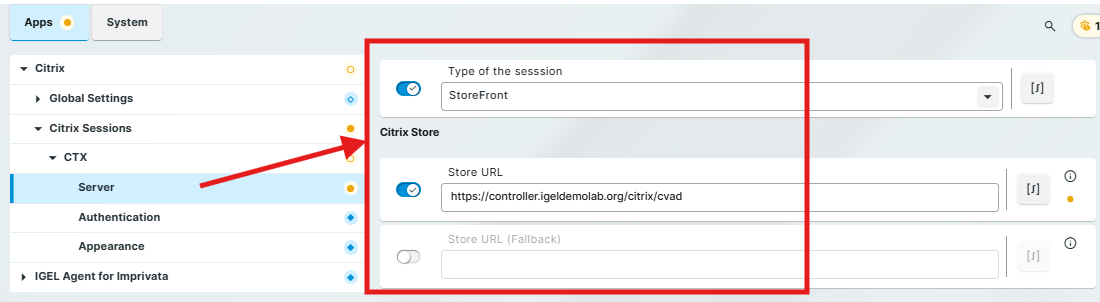
For a Citrix Client Auth Only session, the settings under Apps > Citrix > Citrix Sessions > [session name] > Authentication should look like this:
Authentication Method: Set to IGEL Login
Remember user name and domain: Disable or set to inactive
Synchronize Citrix password with screenlock: Disable or set to inactive
Set inactive:
Username
Domain
Password
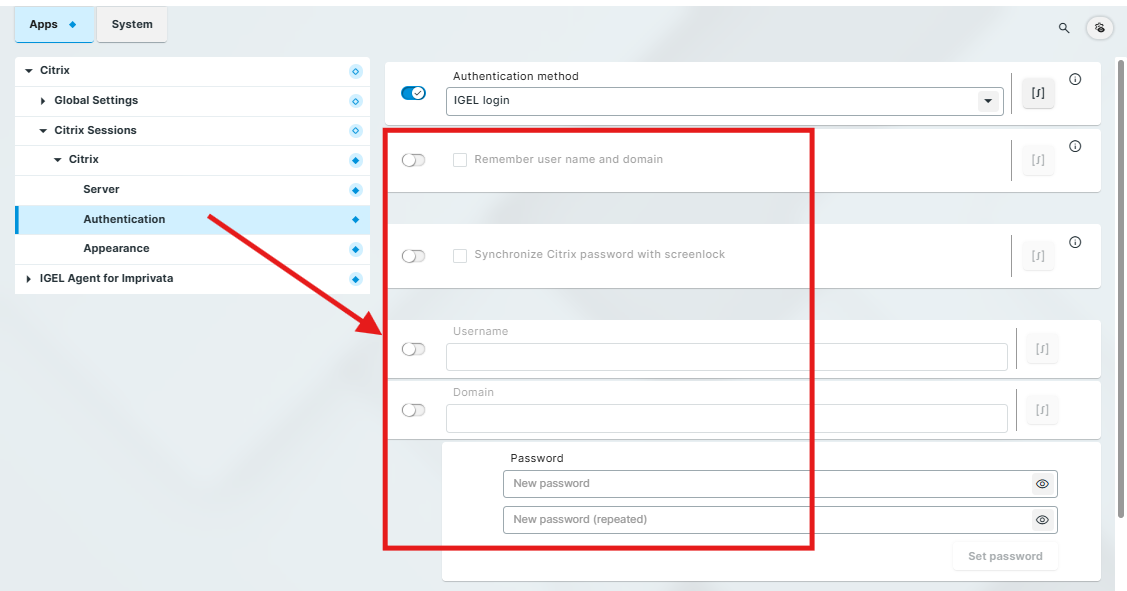
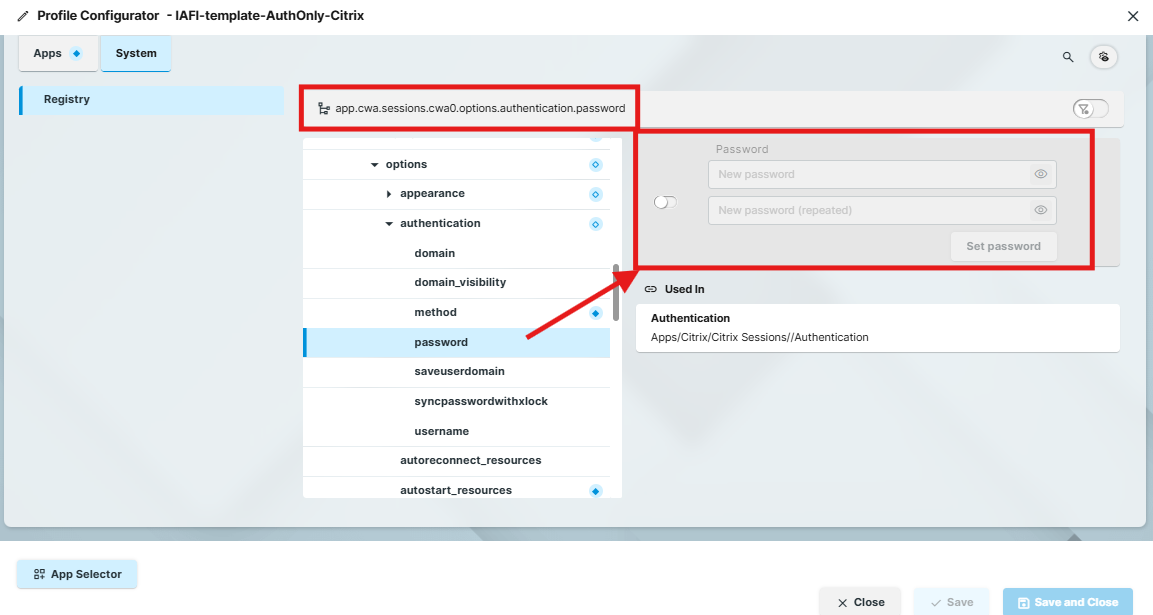
IMPORTANT: For Citrix Auth Only, you have to disable the Password field in the application registry.
Query for Kerberos ticket
This is an experimental feature being investigated for future workflows. It is disabled by default.
Generally, this option can be recommended for a Chromium session in an on-premises environment. When Azure Entra ID is used, this might result in a delay due to a timeout.
☑ After successful authentication with the IGEL Agent for Imprivata, the agent requests a ticket from the local Active Directory (AD).
☐ No Kerberos ticket will be requested. (default)
Configuring Fast User Switching (FUS)
Starting with the IAFI 1.0.0 version, we changed the FUS configuration to support standalone IGEL sessions (ex: Citrix, Horizon, AVD).
The FUS configuration is primarily for Imprivata Epic workflows with an IAFI lock screen used to obscure the session.
In the profile configurator, go to Apps > IGEL Agent for Imprivata > Fast User Switching.
Edit the settings according to the FUS workflow you are configuring. The parameters are described as follows:
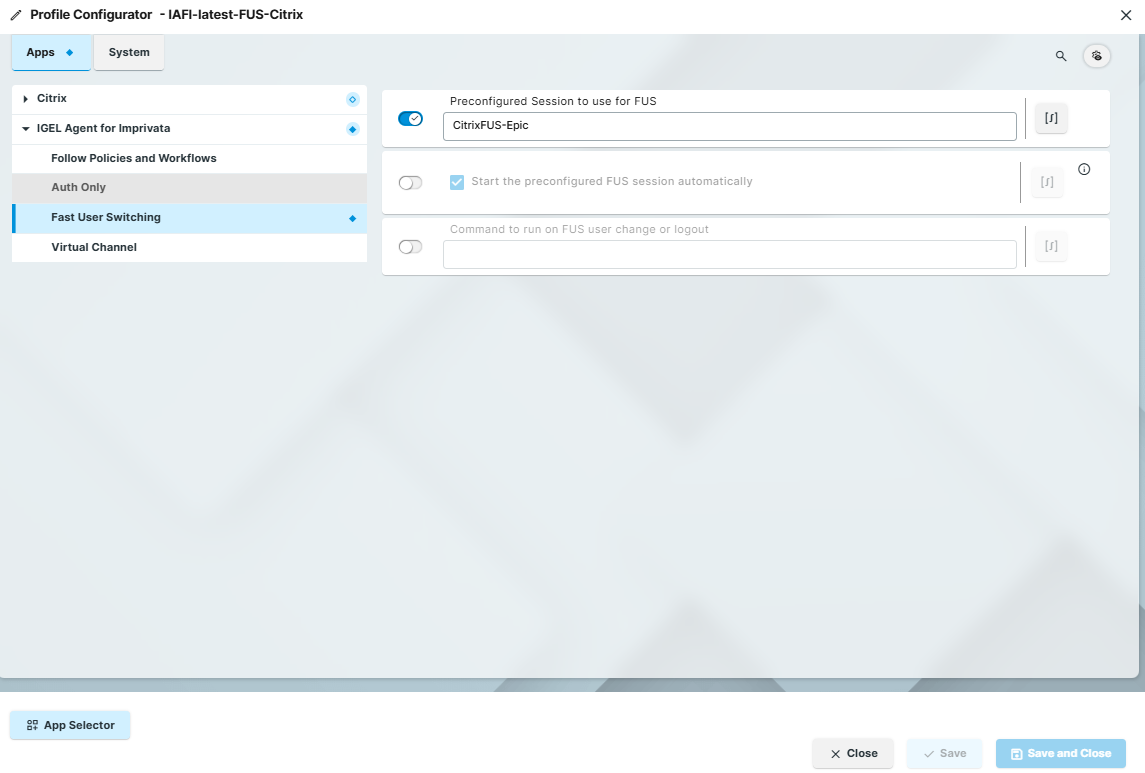
Preconfigured Session to use for FUS
Enter the name of a preconfigured session.
The preconfigured session would be for launching Epic or a Published Desktop. This session would be configured using generic credentials (ex: HOSTNAME).
Start the preconfigured FUS session automatically
☑ Enabled (Default)
☐ Disabled
With this setting enabled, when IAFI starts, it will automatically launch the preconfigured session. Once the virtual channel is established between IAFI and the Imprivata agent on the remote session, IAFI will show an authentication dialog indicating the user can log in.
Once the user logs into IAFI, their identity will be passed over the virtual channel to log the user into Epic
Command to run on FUS user change or logout
Enter a command that can be used to close a local application such as Chromium when a user logs out or during a user switch.
Configuring Virtual Channel
By default, all of the Imprivata Virtual Channel settings are enabled for the supported session types (Citrix, Horizon, Microsoft AVD, Windows 365 Cloud PC, RDP).
Supported protocols are ICA, RDP, Horizon Blast and PCoIP.
In the profile configurator, go to Apps > IGEL Agent for Imprivata > Virtual Channel.
Edit the settings according to your needs.
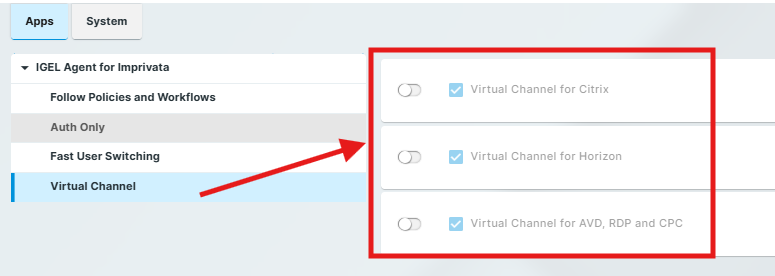
The parameters are described as follows:
Virtual Channel for Citrix
☑ Imprivata's virtual channel is used for the Citrix session. (Default)
☐ Imprivata's virtual channel is disabled for the Citrix session.
Virtual Channel for Horizon
☑ Imprivata's virtual channel is used for the Horizon session. (Default)
☐ Imprivata's virtual channel is disabled for the Horizon session.
Virtual Channel for AVD, RDP and CPC
☑ Imprivata's virtual channel is used for the AVD, RDP, or CPC session. (Default)
☐ Imprivata's virtual channel is disabled for the AVD, RDP, or CPC session.
Registry | Value |
|---|---|
| Virtual Channel for AVD, RDP and CPC - True (default) / False |
| Virtual Channel for Citrix - True (default) / False |
| Virtual Channel for Horizon - True (default) / False |
