Standalone Authentification Method
Prerequisites
The following files are required:
Root certificate and intermediate CA certificates, as applicable
File
cn_mapwhich contains mappings of common names to UPN names for each smartcard certificate
Creating the cn_map File
→ Create a file named cn_map in which each line is in the format <common name> -> <logon name> where
<common name>is the common name part of the certificate's subject
Example from a client certificate: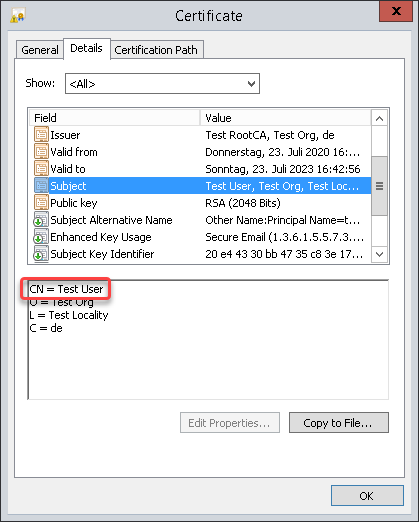
<logon name>is the UPN name of the SubjectAltName extension of the certificate. The UPN name is dependent on whether Enterprise Kerberos names are enabled or disabled (the setting is described under Configuring the Devices):When Enterprise Kerberos names are enabled, the user domain may differ from the default domain. In the following example, the user's domain is
test.mail, while the default domain isMY.DOMAIN:testuser@test.mail@MY.DOMAIN
Example from a client certificate: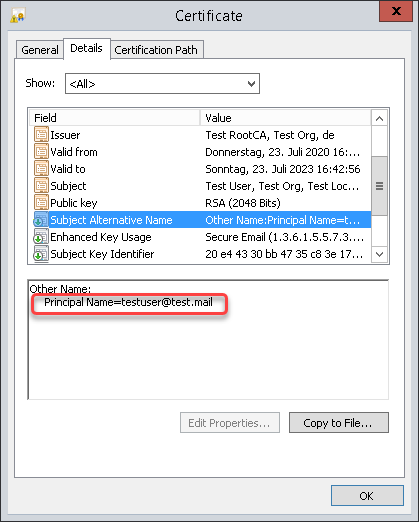
When Enterprise Kerberos names are disabled, the user domain is the same as the default domain. Example:
testuser@MY.DOMAIN
Example line: Test User -> testuser@test.mail@MY.DOMAIN
Transferring the cn_map File to the Devices
The cn_map file must be located in the directory /etc/pam_pkcs11/cn_map. This can be achieved via UMS file transfer.
To transfer the cn_map file to the devices:
In the UMS structure tree, go to Files and in the context menu, select New file.
In the New file dialog, configure the settings as follows:
Local file: Local file path of the certificate. Use the file chooser by clicking
 .
.Device file location:
/etc/pam_pkcs11/cn_map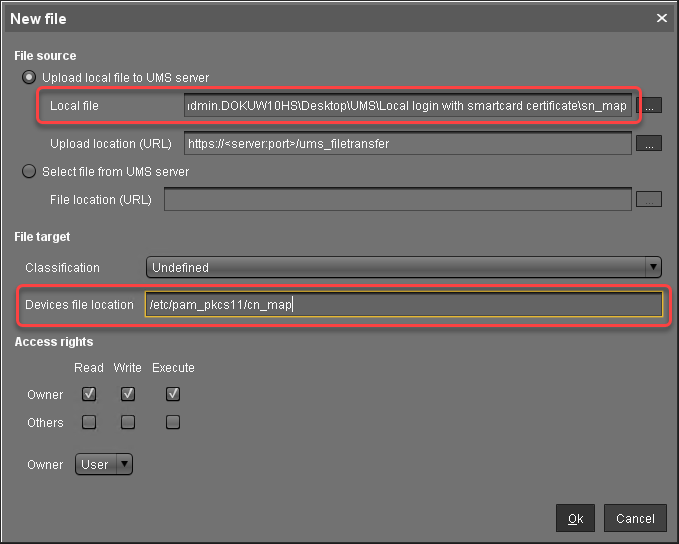
Click Ok.
The file object is created in the UMS.In the UMS structure tree, select the endpoints for which you want to configure the local login with a smartcard certificate. For mass deployment, it is recommended to use a directory containing the endpoint devices or a profile (see Creating Profiles).
In the Assigned objects area, click
 .
.Under Files, select the file object using the
 button:
button: 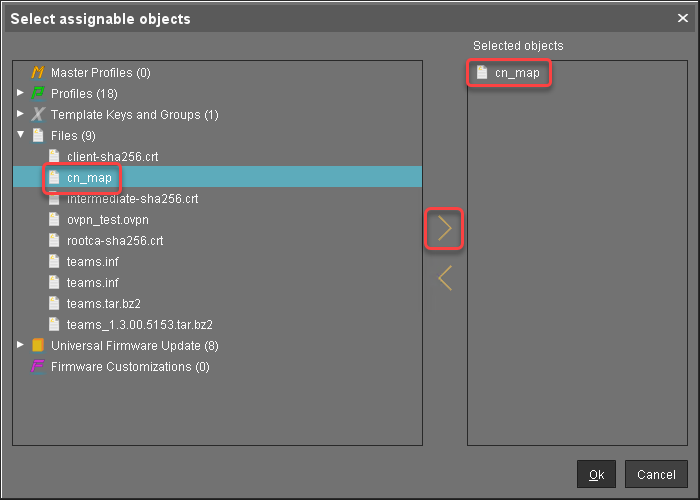
Click Ok.
In the Update time dialog, select Now and click Ok.
Thecn_mapfile is transferred to the endpoint device.
Transferring the Certificate Files to the Devices
Registering the Certificate Files as File Objects
To transfer the certificate files to the devices, perform the following steps for each certificate file:
In the UMS structure tree, go to Files and in the context menu, select New file.

In the New file dialog, configure the settings as follows:
Local file: Local file path of the certificate. Use the file chooser by clicking
 .
.Device file location:
/etc/pam_pkcs11/cacerts/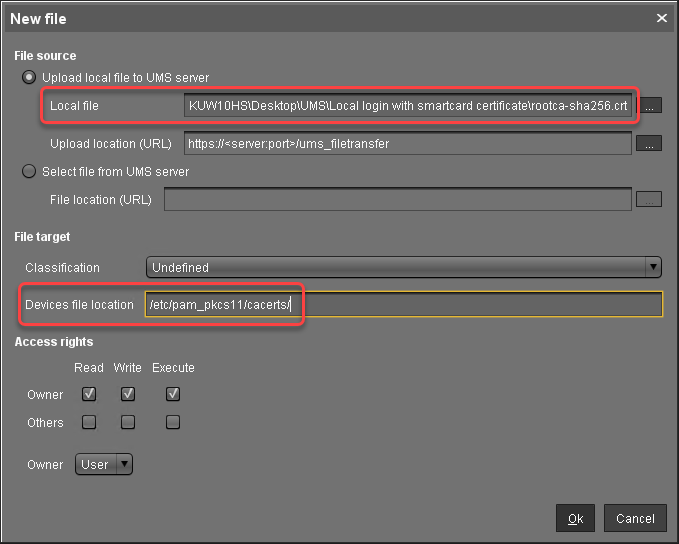
Click Ok.
The file object is created in the UMS.
Assign the Certificate Files to the Devices
In the UMS structure tree, select the endpoints for which you want to configure the local login with a smartcard certificate. For mass deployment, it is recommended to use a directory containing the endpoint devices or a profile (see Creating Profiles).
In the Assigned objects area, click
 .
.Under Files, select the required file objects using the
 button:
button: 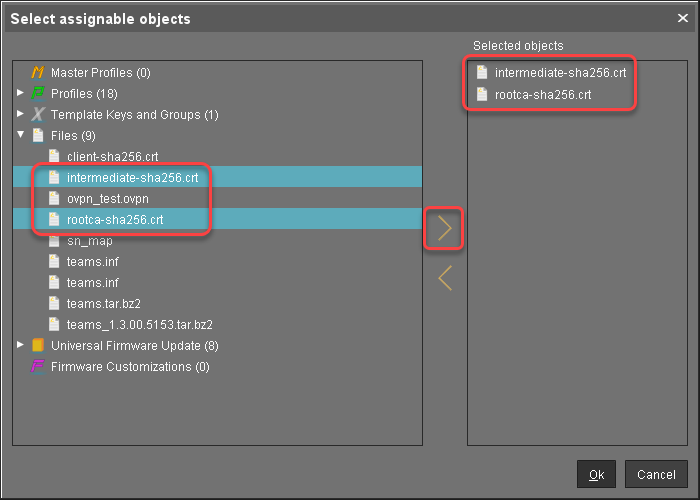
Click Ok.
In the Update time dialog, select Now and click Ok.
The certificates are transferred to the endpoint device.
Configuring the Devices
To enable local login with a smartcard certificate, you must configure the devices appropriately. For mass deployment, it is recommended to use a profile.
Go to Security > Smartcard > Middleware and select the middleware to be used.
Go to System > Registry > auth > login > pkcs11 (registry key:
auth.login.pkcs11) and activate Login with smartcard certificate.Go to System > Registry > auth > login > pkcs11_cert_policy (registry key:
auth.login.pkcs11_cert_policy) and enter the methods for certificate verification that are to be used. For further information, see the documentation in https://github.com/OpenSC/pam_pkcs11.If Kerberos enterprise names are used, go to System > Registry > auth > login > krb5_enterprise and activate Allow enterprise names.
Debugging
→ If you need to debug the smartcard certificate login, go to System > Registry > auth > login > pkcs11_debug (registry key: auth.login.pkcs11_debug) and activate Enable debugging of smartcard certificate login.
Logging messages will be available via syslog.
