F5 BIG IP: Example Configuration as Reverse Proxy in IGEL UMS with SSL Offloading
In this article. you can find an example configuration of F5 BIG IP for SSL Offloading in the IGEL Universal Management Suite (UMS).
General compatibility is tested with the configurations described in this article. There could be different ways to do the configuration.
As the reverse proxy is an external software we cannot provide full support for each version.
Requirements
Requirements for UMS and certificate configuration for reverse proxy are summarized in Configure the UMS to Integrate Reverse Proxy with SSL Offloading.
To use remote management functions over the F5 BIG IP Reverse Proxy, you need to use IGEL OS 12.3.2 or higher and UMS 12.04.120 or higher.
The reason for this is that F5 BIG IP did not support the EC key used in the device certificate, so this was changed to RSA keys starting from these versions. (The device certificate key type can be changed in IGEL Setup using the registry key system.remotemanager.device_key_type.)
Process Overview
The configuration tasks of F5 BIG IP are:
UMS / ICG configuration and certificate export as described in Configure the UMS to Integrate Reverse Proxy with SSL Offloading
UMS certificate management (Web UMS and EST CA)
UMS backend node and pool configuration
iRule configuration for client certificate forwarding
SSL client profile configuration
SSL server profile configuration
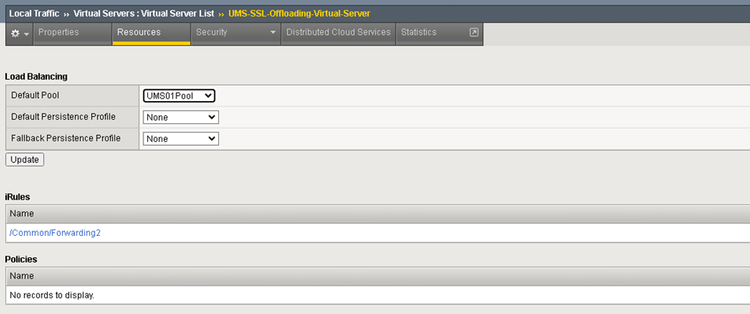
Virtual server configuration
Certificate Management
The certificates created in Configure the UMS to Integrate Reverse Proxy with SSL Offloading must be added in the F5 BIG IP application. BIG IP offers a common Certificate Management.
To configure the UMS Web Certificates / Keys:
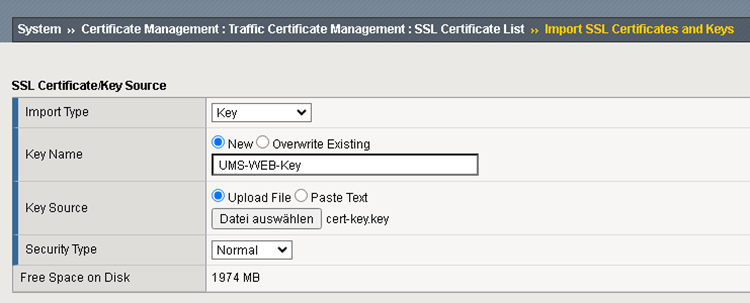
Add UMS Web Private Key.
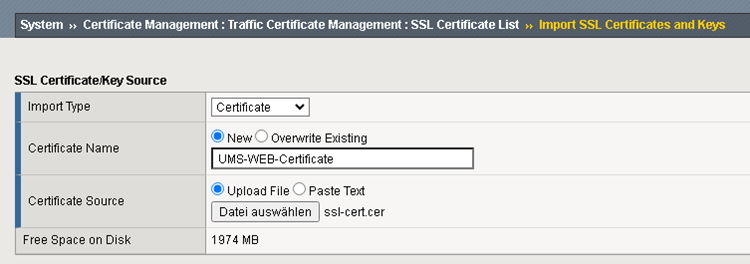
Add UMS Web Certificate.
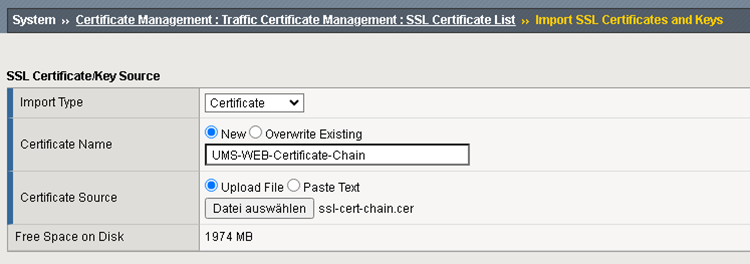
Add UMS Web Certificate Chain.
Add UMS EST CA Certificate
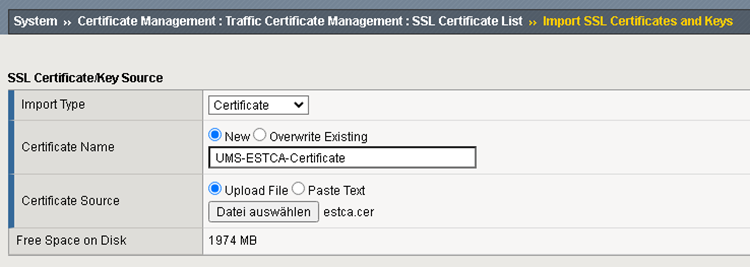
Verify that you have all the imported certificates.
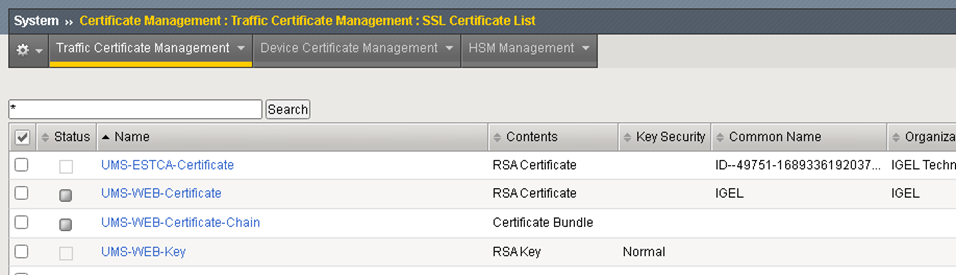
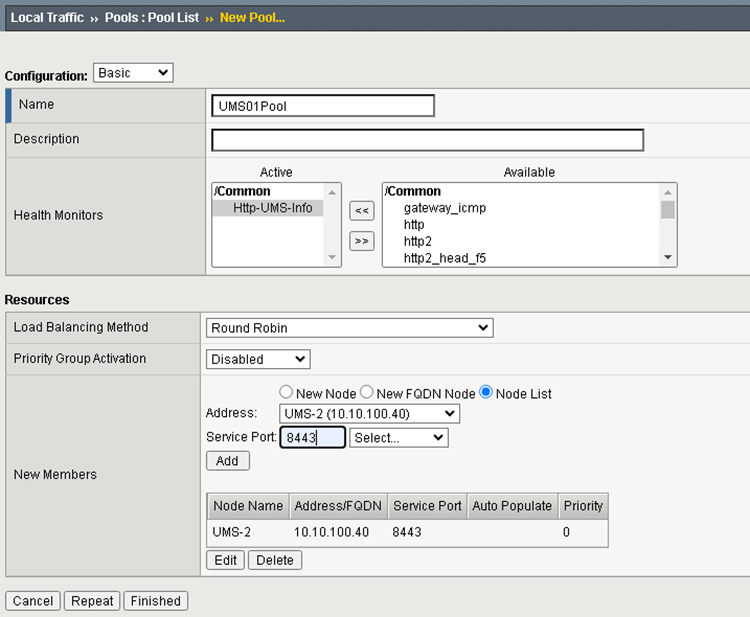
Backend Node and Pool Configuration
The UMS Server must be configured as backend server.
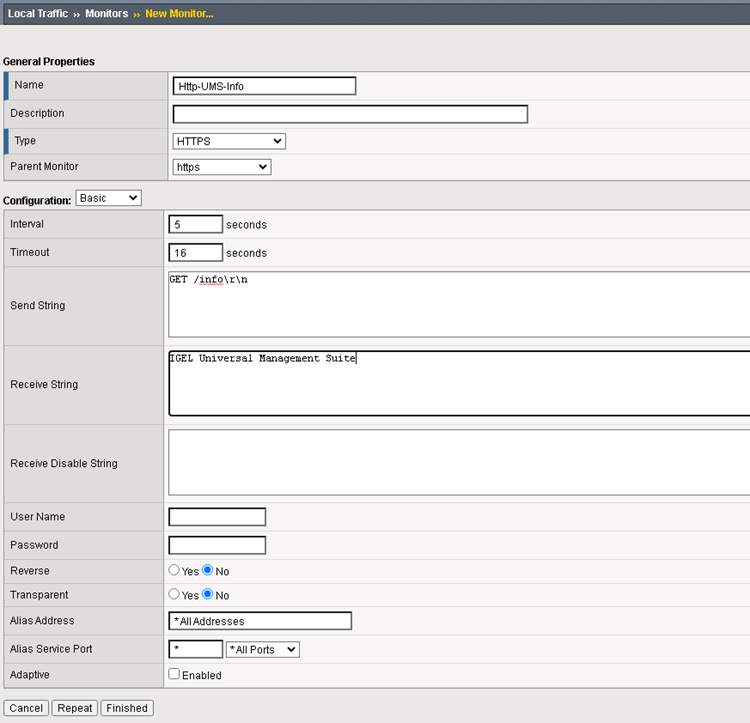
Add a Monitor and configure it for testing if the UMS info URL is online.
The following properties must be set:Type
HTTPS
Send String
GET /info\r\n
Receive String
IGEL Universal Management Suite
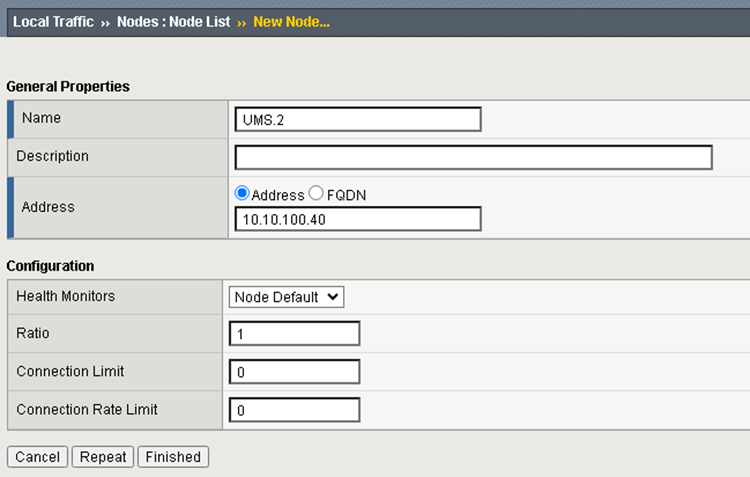
Create a new Node and set the Address of the UMS Server.
Add Pool. In the pool configuration the monitor and the node server must be at least configured. There is no specific Load Balancing Method recommended.
IRULE Configuration to Forward the Client Certificate in HTTP Header
Irules is the Script support of F5 BIG-IP.
The Client Certificate can be read from the HTTP_REQUEST. The variable [X509::whole [SSL::cert 0]] contains it in PEM format.
The UMS expects the certificate URL Encoded so it must be encoded: [URI::encode $ssl_cert]
Forwarding Header Example:
when HTTP_REQUEST {
set DEBUG 1
if { [SSL::cert count] > 0 } then {
set ssl_cert [X509::whole [SSL::cert 0]]
set encodedCert [URI::encode $ssl_cert]
HTTP::header insert "X-SSL-CERT" "$encodedCert"
if { $DEBUG } {
log local0. "Client Certificate: $ssl_cert"
log local0. "Client Certificate Accepted: [X509::subject [SSL::cert 0]]"
log local0. "Client inserted"
log local0. [HTTP::header names]
}
} else {
log "No Client SSL Certificate!"
}
}SSL Client Profile Configuration
The SSL Client Profile is used to set the SSL configuration for all incoming requests to the Virtual Servers.
Add a new SSL Client Profile and Configure according to the picture below.
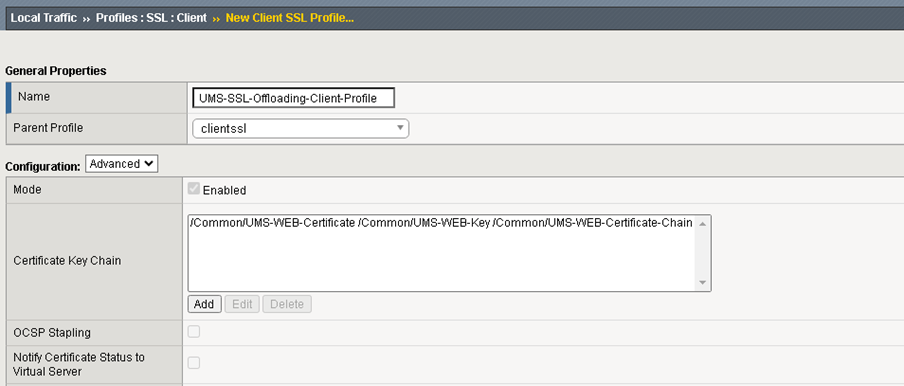
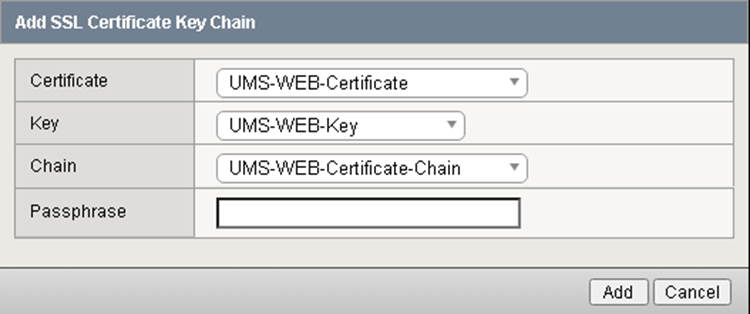
Configure the UMS WEB Certificates and Key.
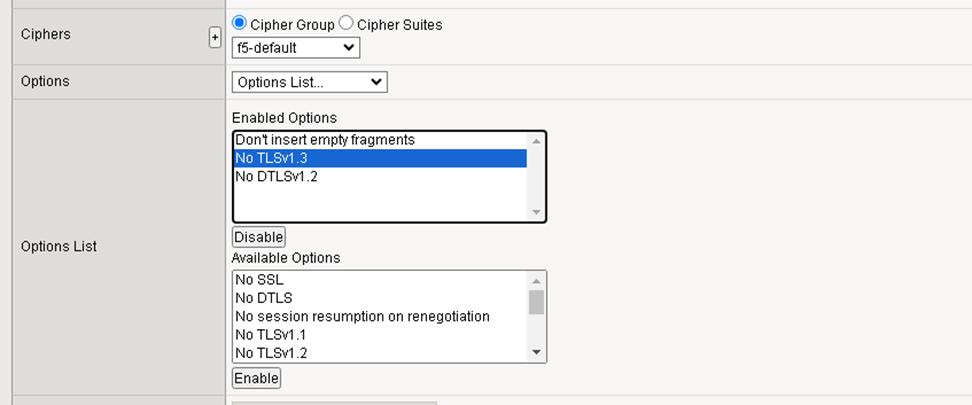
TLSv1.3 is used in the connection from the Device to UMS so the ciphers must be customized.
Ciphers
f5-default can be used as Cipher Group
Options List
disable the “No TLSv1.3” entry in the Enabled Options list
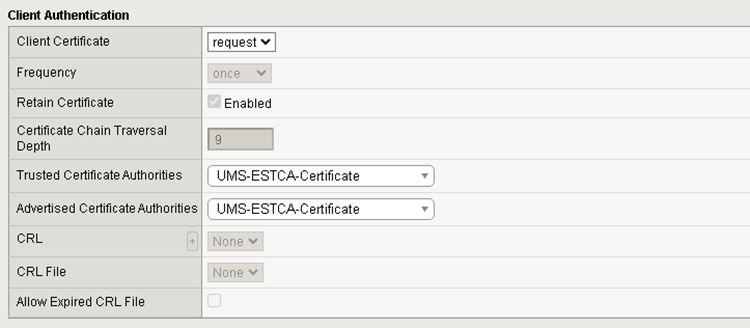
The necessary customizations for Client Certificate Authentication are:
Client Certificate
This value must be set to request
Trusted Certificate Authorities
Set to UMS-ESTCA-Certificate
Advertised Certificate Authorities
Can be set to UMS-ESTCA-Certificate
SSL Server Profile Configuration
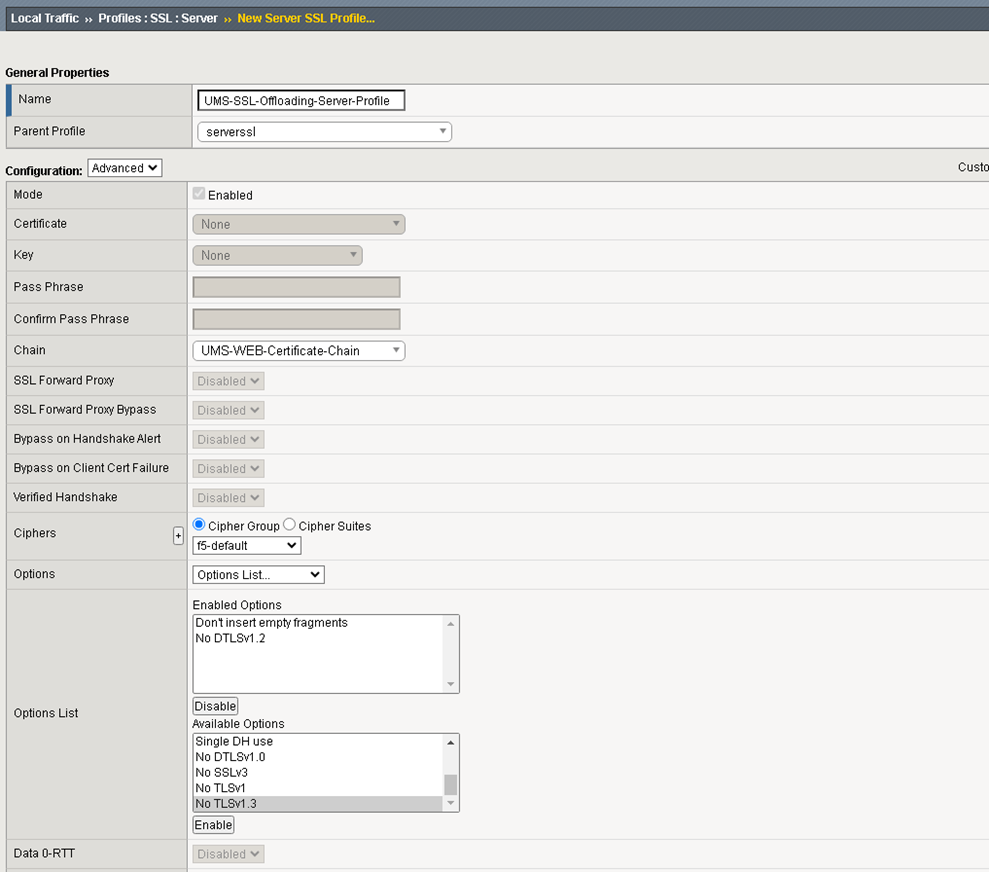
The SSL Server Profile is used to set the SSL configuration for all requests to the Backend Servers (UMS).
Create a new SSL Server Profile.
Set the Chain value to UMS Web Certificate Chain.
Set the TLSv 1.3 configuration the same as for the SSL Client Profile above.
Virtual Server Configuration
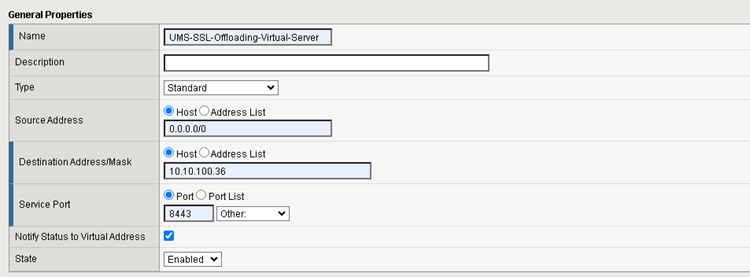
The Virtual Server defines the Listener in F5 BIG-IP.
Set the following values:
Type
Standard
Source Address
From which IP are requests allowed. Set it to * if this shouldn’t be evaluated
Destination Address
The Address under which this Virtual Server is reachable
Service Port
Select the UMS Port
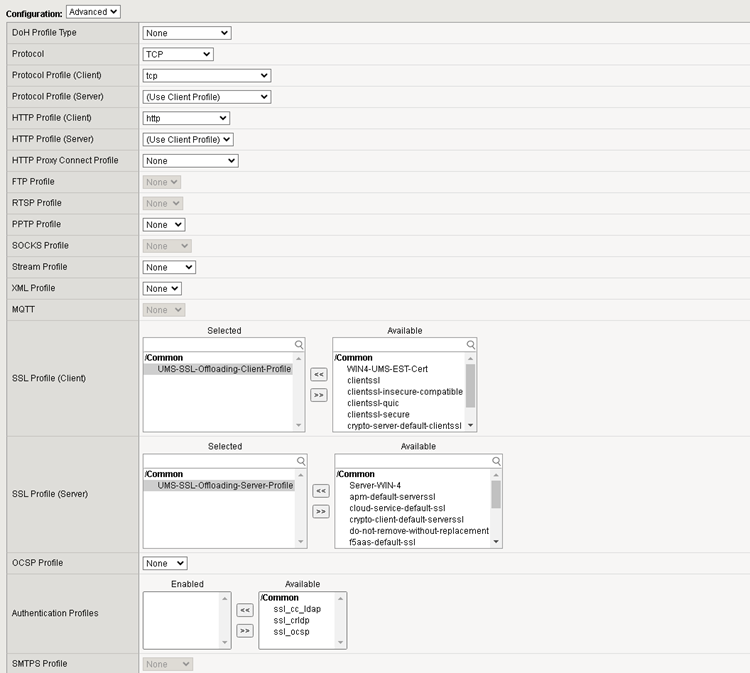
Protocol
TCP
HTTP Profile
http, required to evaluate the HTTP Header
SSL Profile (Client)
Add the earlier created Client SSL Profile
SSL Profile (Server)
Add the earlier created Server SSL Profile
Source Address Translation
Set it to Auto Map
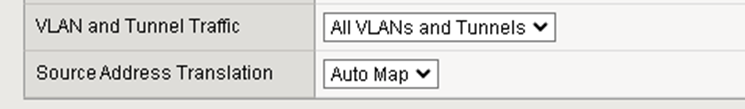
Add the Pool and iRule to the Virtual Server.