Configuring an AD Connection
Perform the following steps to set up the connection between the UMS and the Active Directory of your company.
If you have user and group dependencies between different configured domains/subdomains, then you might want to activate Include all configured AD domains for search and import of AD users / groups. This option activates the group search for a user within all configured domains. On activation, a confirmation dialog is shown.
If this option is activated, a user may gain additional permissions. This will be the case if
the user is in a group that has been discovered due to this option,
this group has been imported under System > Administrator accounts,
and permissions have been assigned to this group i.e. permissions the user would not have otherwise.
Please note that, due to the additional lookups, this option might have an impact on the performance in the following areas:
UMS login
Permission dialogs
Shared Workplace (SWP)
Click Add (+) under UMS console > UMS Administration > Global Configuration > Active Directory / LDAP.
The Add Active Directory / LDAP Service dialog opens.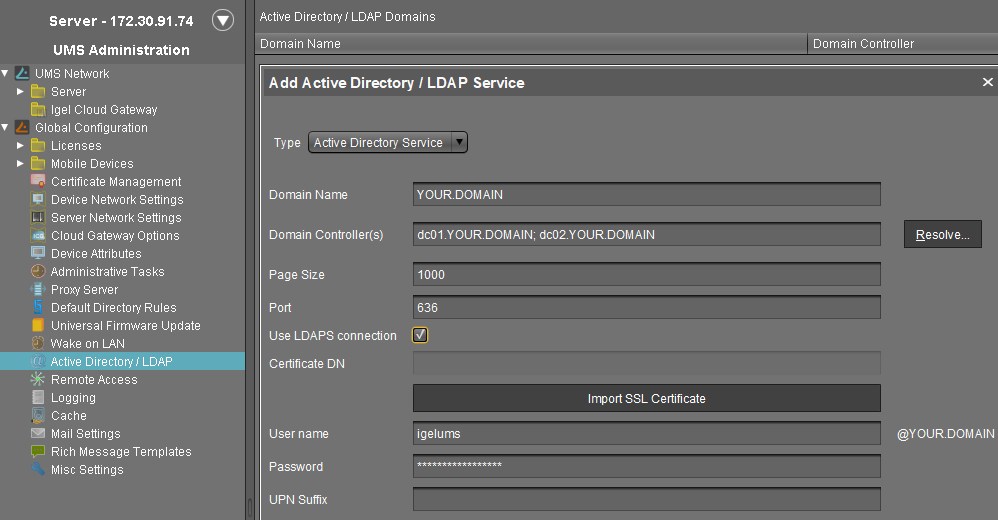
Select Active Directory Service as Type.
Enter the Domain Name.
Several Active Directories can be linked. You should therefore ensure that you provide the correct domain when logging in (e.g. to the UMS console).
Enter the Domain Controller(s) manually or click Resolve... for the automatic search.
To separate domain controllers, use a semicolon.
If the option Use LDAPS connection (see below) is enabled, make sure that a fully qualified name of the Domain Controller has been entered. See Troubleshooting: Problems When Configuring an Active Directory with LDAP over SSL .
Enter Page Size.
The Page Size property sets the maximum number of items in each page of results that will be returned by a search. It affects query performance, but not the number of overall results. The standard value is "1000". Change this value in line with your server configuration.Activate Use LDAPS connection to secure the connection with the provided certificate.
The Port changes automatically to default "636".Click Import SSL Certificate to configure the certificate and to verify the Certificate DN.
Since the name of the Domain Controller is checked against the certificate, they must correspond.
If more than one domain controller is used, the root certificate of the domain must be configured. See Troubleshooting: Problems When Configuring an Active Directory with LDAP over SSL .
The supported certificate extensions are .cer, .pem and .der; the format is Base64.
Under User name and Password, enter your user credentials. This user must have read access in Active Directory.
Please pay attention to upper and lower case when entering the username.
Enter UPN Suffixes (aliases) if you have defined any (semicolon separated list). Example:
domain.local;test.local
The settings must correspond to the configuration of the Active Directory. If there are registered UPN suffixes in the AD, they should be known also by the UMS.
Click on Test Connection to check that you have entered a valid configuration.
Click Ok to confirm your settings.
The Active Directory domain is listed under Active Directory / LDAP Domains.