Azure Application Gateway: Example Configuration as Reverse Proxy in IGEL UMS with SSL Offloading
This article describes the IGEL Unified Management Suite (UMS) configurations and the Azure Application Gateway configurations you need for SSL Offloading.
General compatibility is tested with the configurations described in this article. There could be different ways to do the configuration.
As the reverse proxy is an external software we cannot provide full support for each version.
Requirements
Requirements for UMS and certificate configuration for reverse proxy are summarized in Configure the UMS to Integrate Reverse Proxy with SSL Offloading.
Process Overview
The configuration tasks of the reverse proxy are:
UMS / ICG configuration and certificate export as described in Configure the UMS to Integrate Reverse Proxy with SSL Offloading
Azure application gateway creation
Routing rule creation for onboarding connection
Routing rule creation for the Websocket connection
Network security group check
Mutual authentication creation for WebSocket connection
Rewrite configuration for client certificate forwarding
Troubleshoot certificate error (if needed)
Create Azure Application Gateway
Assign correct Virtual network and Subnet.
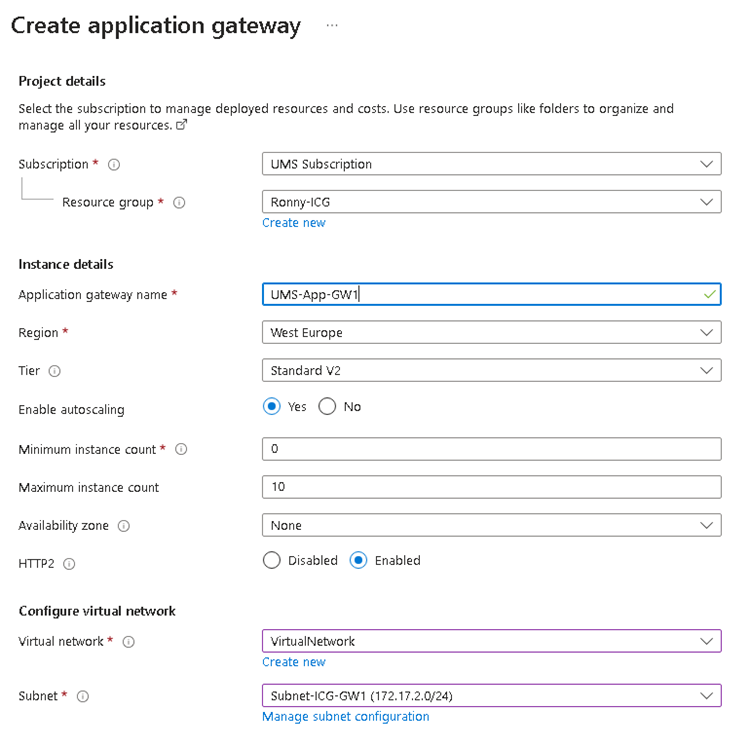
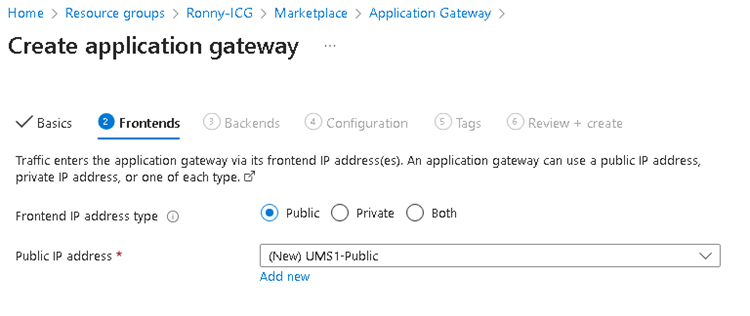
Provide Frontend IP address.
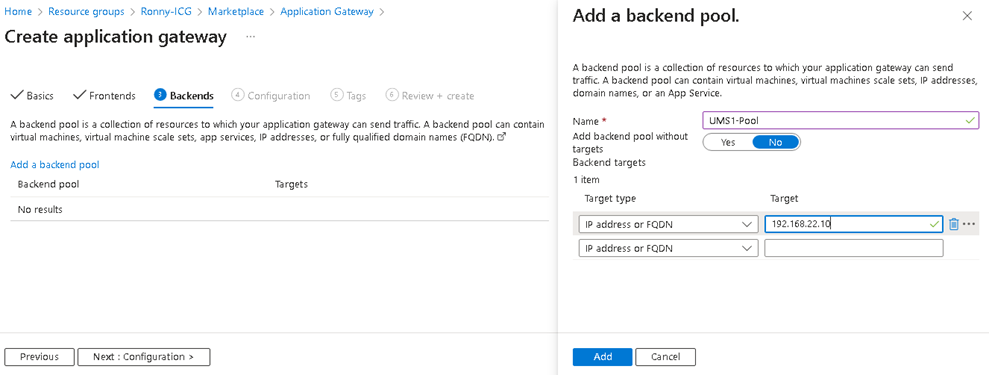
Add backend pool with UMS address. Add the UMS / ICG FQDN or IP.
Add a Routing Rule for Onboarding Connection
Configure a listener:
Set the Protocol to HTTPS.
Set the Public IP address.
The recommended Port value is 443.
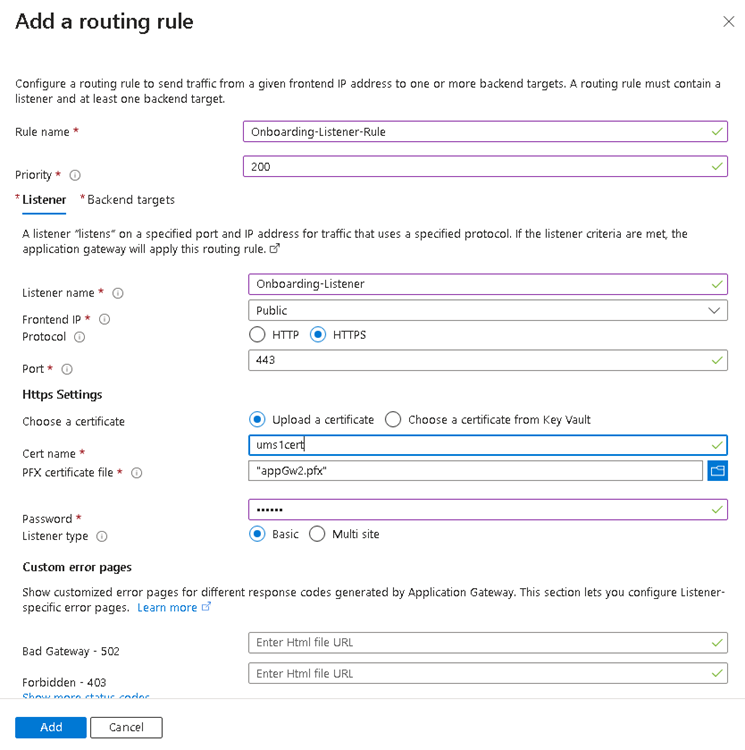
Select the
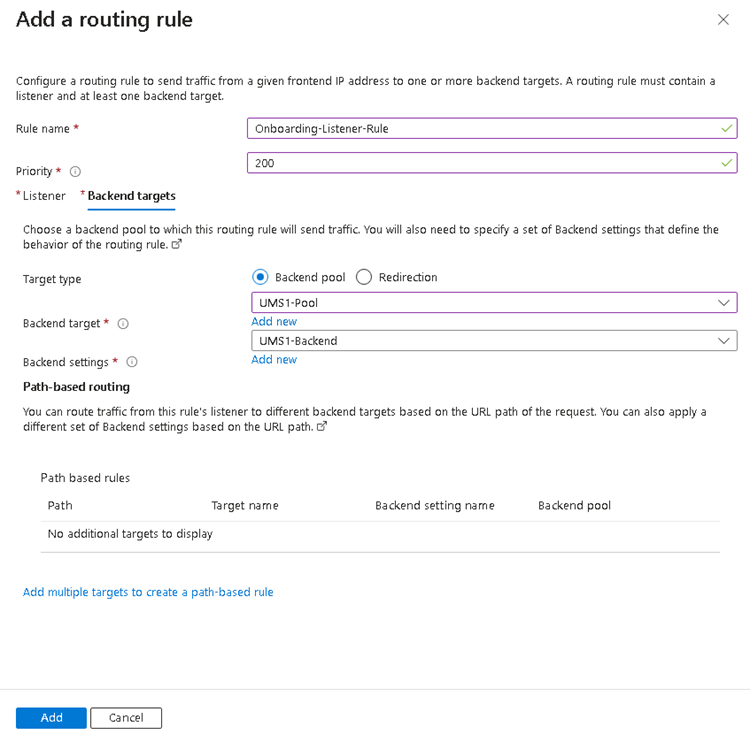
PFXfile created in Configure the UMS to Integrate Reverse Proxy with SSL Offloading and enter the appropriate password.Configure Backend targets. The already inserted Backend pool can now be selected and the Backend settings must be added.
Under Add Backend settings, set the Backend protocol to HTTPS and add the UMS Web Port as Backend port.
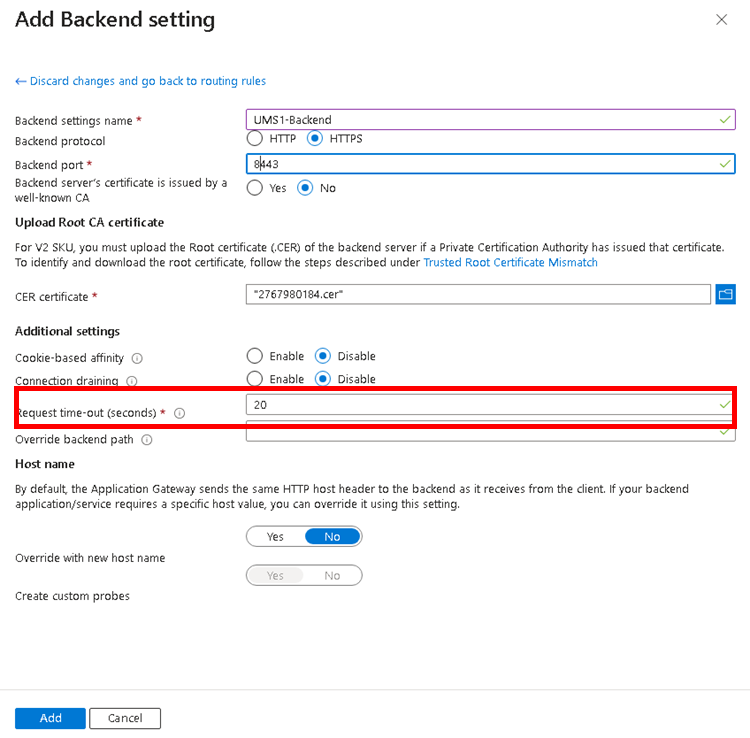
Select the UMS Web/Cloud Gateway Root Certificate exported in Configure the UMS to Integrate Reverse Proxy with SSL Offloading.
Set the value for Request time-out (seconds) to a value at least 130 seconds.
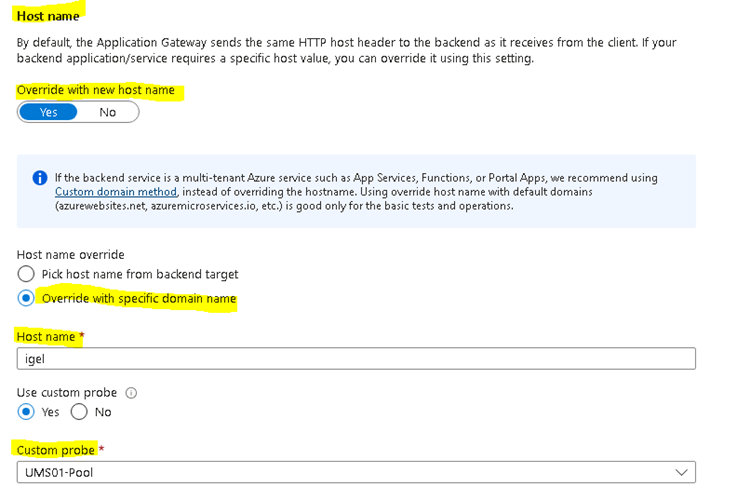
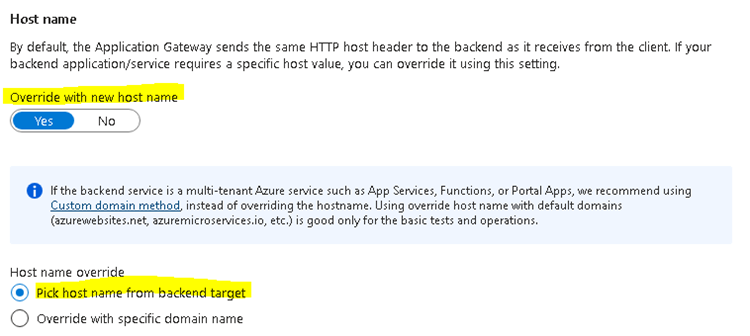
Verify that the Override with new host name is activated and set Host name override.
Set a Custom probe.

Custom Probe Settings: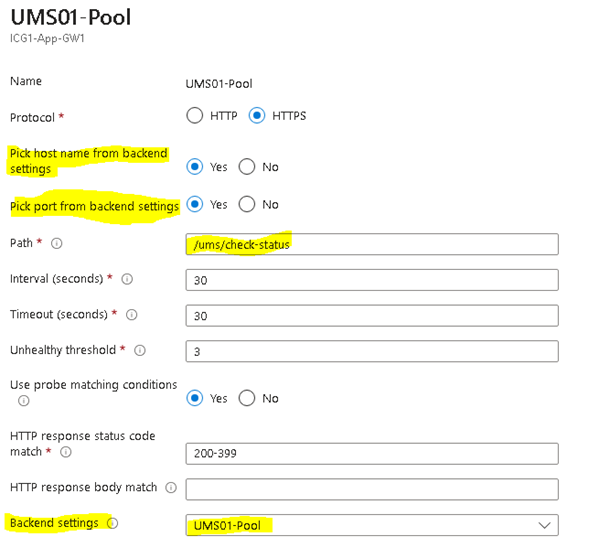
Add a Routing Rule for the Websocket Connection
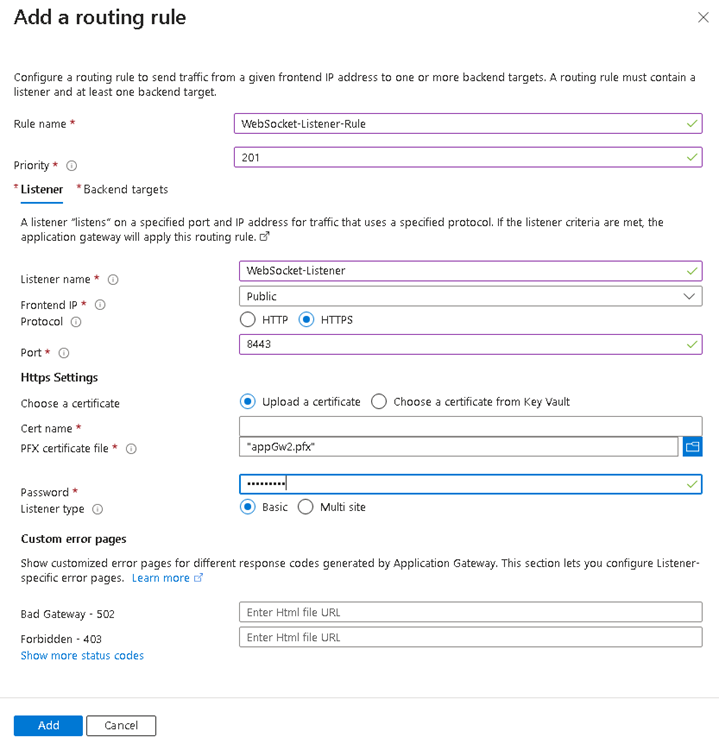
Configure a listener:
Set the Protocol to HTTPS.
Set the Public IP address.
The recommended Port value is 8443.
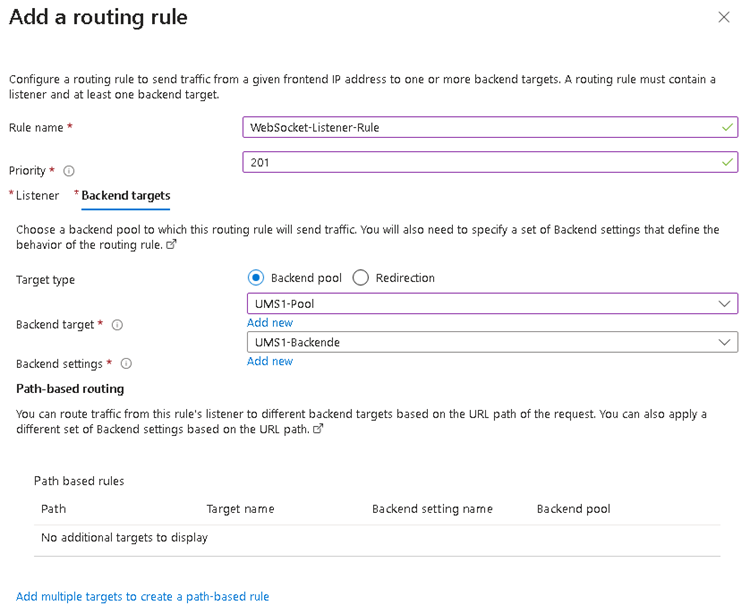
Select the
PFXfile created in Configure the UMS to Integrate Reverse Proxy with SSL Offloading, and enter the appropriate password.Add the same Backend Settings as for the Onboarding connection.
Check Network Security Group
Open the Network Security Group used for the Gateway Network and verify if the used Ports are listed
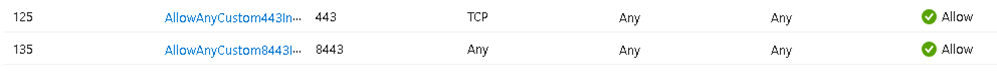
If they are not listed, add them.
Set Mutual Authentication for WebSocket Connection
The mutual authentication can be set in Azure Application Gateway with SSL Profiles:
Add an SSL Profile under SSL settings.
In the Client Authentication part of the Dialog the EST CA Certificate is required, that was exported from the UMS.
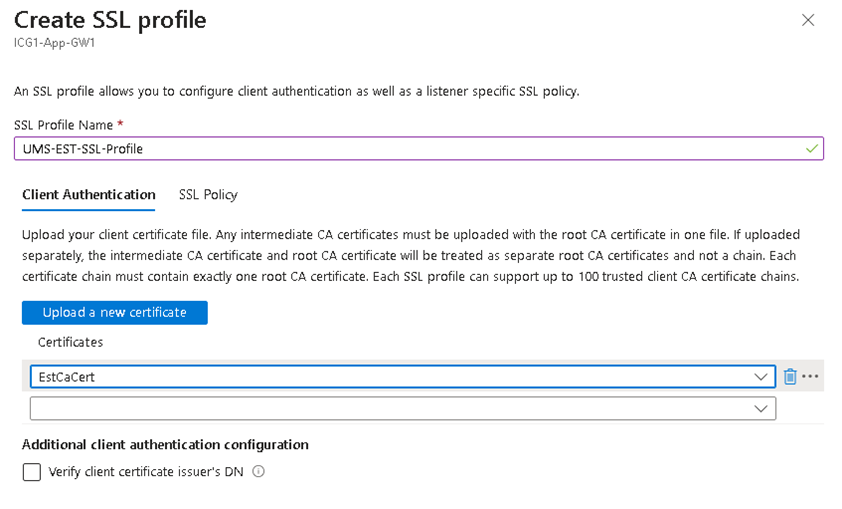
Add the SSL profile to the WebSocket listener. Not to the Onboarding listener!

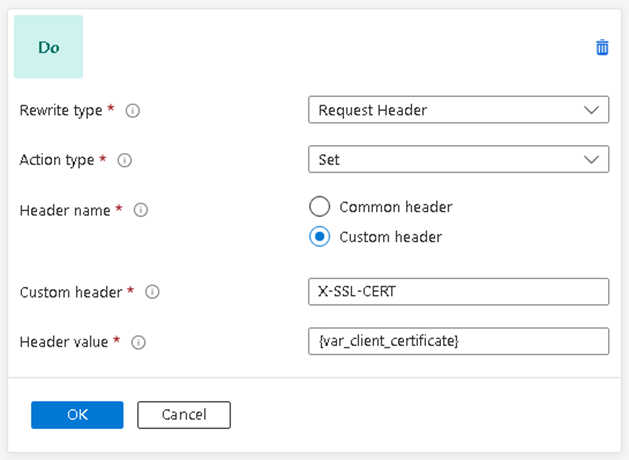
Add a Rewrite for Client Certificate Forwarding
The client certificate must be forwarded to the UMS. The Application Gateway can be configured to forward it by a rewrite definition.
Create a rewrite set and assign it to the appropriate rule.
Add the following rewrite rule:
Troubleshooting Certificate Error: Common Name Does Not Match
The UMS or ICG certificate must contain the FQDN of the Backend Server as the Common Name. This value is mandatory for the Azure Application Gateway connection to the Backend. The following error occurs if the certificate is wrong.
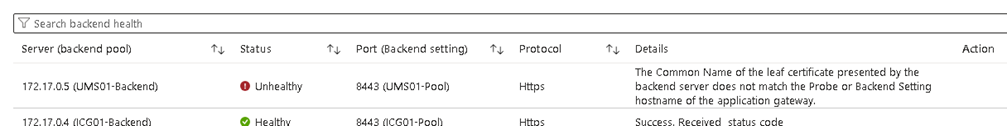
In case the Common name cannot be adjusted, it is possible to adopt the Hostname of the UMS / ICG in the Backend Settings. In this case a custom probe must be defined with the given Host name value.