Cloud Gateway Certificates in the IGEL UMS
Here, you can manage the certificates for the communication between the IGEL Cloud Gateway (ICG) and the endpoint devices.
Menu path: UMS Administration > Global Configuration > Certificate Management > Cloud Gateway
For details of how to set up all components for a connection to the ICG, see IGEL Cloud Gateway > ICG Manual > IGEL Cloud Gateway Installation and Setup.
Use
IGEL Cloud Gateway > ICG Manual > Administration > How to Exchange the Root Certificate for ICG
IGEL Cloud Gateway > ICG Manual > Administration > Renewing a Signed Certificate for the ICG
Possible Actions
![]() - Create a root certificate.
- Create a root certificate.
![]() - Import a root CA certificate.
- Import a root CA certificate.
![]() - Create a signed certificate from the CA certificate (root or intermediate) that is currently selected.
- Create a signed certificate from the CA certificate (root or intermediate) that is currently selected.
![]() - Remove the selected certificate from the UMS. Only certificates that are not currently in use can be removed.
- Remove the selected certificate from the UMS. Only certificates that are not currently in use can be removed.
![]() - Export the selected end certificate and its complete certificate chain to a keystore in the IGEL Cloud Gateway keystore format.
- Export the selected end certificate and its complete certificate chain to a keystore in the IGEL Cloud Gateway keystore format.
![]() - Show the content of the selected certificate.
- Show the content of the selected certificate.
![]() - Navigate to an IGEL Cloud Gateway that is using the selected certificate.
- Navigate to an IGEL Cloud Gateway that is using the selected certificate.
Generate root certificate
Display name: Name in the root certificate (common name, CN).
Your organization: Organization, company, government agency.
Your locality (or random identifier): The location of the organization.
Your two-letter country code: ISO 3166 country code, e.g. DE for Germany.
Valid until: Local date on which the certificate expires. (Default: in 20 years)
Import root certificate
The file selection window opens, allowing you to select the certificate file.
Create a signed certificate
Display name: Name in the certificate (common name, CN).
Your first and last name: Name of the certificate holder.
Your organization: Organization, company, government agency.
Your locality (or random identifier): The location of the organization.
The name in a signed certificate must be different from the one in the root certificate with which it is signed. UMS provides a warning in this case:
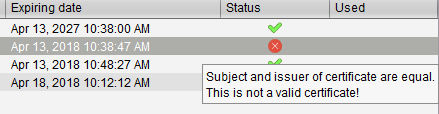
Your two-letter country code: ISO 3166 country code, e.g. DE for Germany.
Host name and/or IP of certificate target server: Host name(s) and IP address(es) for which the certificate is valid. Multiple entries should be separated by a semicolon. To generate a wildcard certificate, use the asterisk, e.g. *.example.com.
Valid until: Local date on which the certificate expires. (Default: in a year)
Certificate type
Possible options:
CA Certificate: The certificate can be used to sign other certificates, but it cannot be used by the ICG.
End Entity: The certificate can be used by the ICG, but it cannot be used to sign other certificates.
Context menu (root certificate)
Create signed certificate: Collects certificate data and signs them with the selected root certificate.
Import signed certificate: Imports a certificate that was already signed outside the UMS by the imported CA.
Import decrypted private key: Imports a private key file.
If the private key is protected with a passphrase, you must decrypt it on the command line with OpenSSL before importing it: openssl rsa -in encrypted.key -out decrypted.key
Remove certificate: Deletes the certificate from the UMS.
Export certificate chain in the IGEL Cloud Gateway Keystore format: Produces a file for ICG installation program.
Export certificate: Exports certificate file.
Show certificate content: Shows the content of the certificate in a text window.
