Settings - Change Server Settings in the IGEL UMS Administrator
Using the IGEL Universal Management Suite (UMS) Administrator, you can edit various server settings, e.g. web server port, ciphers, etc.
Default path to the UMS Administrator:
Linux: /opt/IGEL/RemoteManager/RMAdmin.sh
Windows: C:\Program Files\IGEL\RemoteManager\rmadmin\RMAdmin.exe
The IGEL UMS Administrator application can only be started on the UMS Server.
Menu path: UMS Administrator > Settings
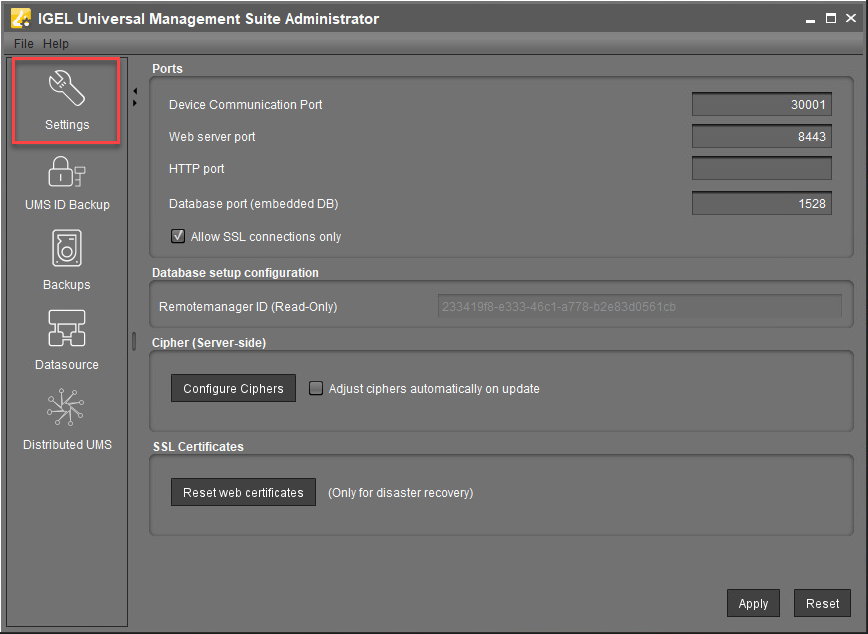
Ports
Device Communication Port: The devices connect to this port. (Default: 30001)
Changes to this port can only be made if you ensure that devices will establish a connection to the new port. For more information on ports, see IGEL UMS Communication Ports.
Web server port: Establishes the connection to the server. This port must be entered in the login window for the IGEL UMS Console or in the URL for the UMS Web App. (Default: 8443)
If the port is changed, the service IGEL RMGUIServer/igelRMserver must be restarted.
If no Cluster Address is configured, the already registered IGEL OS 12 devices won't be manageable anymore after the change of the web server port. Therefore, you will have to register these devices again.
If the change of the web server port is required, it is thus recommended to change the port before registering IGEL OS 12 devices.
HTTP port: If Allow SSL connections only is deactivated, this port is used to reach the UMS via a non-encrypted connection via HTTP. For this to be possible, this port must be specified in the connection URL, e.g. http://<server>:9080/ums_filetransfer/. (Default: 9080)
Database port (embedded DB): Port for communication with the embedded DB. (Default: 1528)
For external databases, the port is defined under Data Sources.
Allow SSL connections only
☑ A connection will only be allowed via SSL. This parameter is activated by default only for new UMS installations starting with UMS version 12.02.100. (Default)
Database Setup Configuration
Remote manager ID (read-only): Unique key for the UMS instance. This is read out automatically.
Cipher (Server-Side)
The cipher configuration is server-specific and excluded from database backups.
If you are using UMS High Availability (HA), the ciphers have to be configured for each server separately.
Configure Ciphers: Use this button to open the Cipher Selection dialog, where you can define which ciphers can be used by the UMS Server.
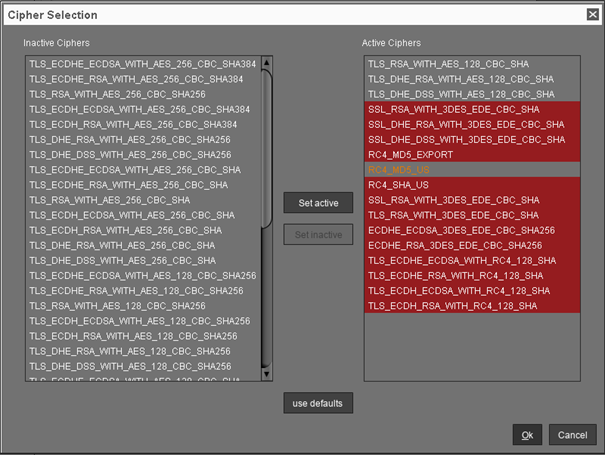
In the Cipher Selection dialog, you can perform the following actions:
Set active: Add the cipher selected in the Inactive Ciphers list to the list of active ciphers.
Set inactive: Remove the cipher selected in the Active Ciphers list from the list of active ciphers.
Use defaults: Restore the default cipher settings.
Ok: Save the changes.
Cancel: Discard all changes.
On new UMS installations, only the default ciphers are activated. By updating the existing UMS installations, the already configured ciphers are kept.
If your server has ciphers from previous installations, there is a possibility that some ciphers are not considered trustworthy any longer.
The levels of security are represented by colors:
Normal display color (black or white, depending on the theme): The cipher is considered trustworthy and is used by Tomcat.
Red color: The cipher is not considered trustworthy and is not used by Tomcat. This cipher cannot be used.
Orange color: The cipher is used by Tomcat but is not considered trustworthy by IGEL or Tomcat or another institution. It is recommended not to use this cipher.
The following example includes ciphers with all 3 levels of security:
Adjust ciphers automatically on update
☑ All new ciphers get activated and all weak ciphers get deactivated automatically on every update.
☐ Cipher configuration is not automatically adjusted on an update.
SSL Certificates
Reset web certificates (Only for disaster recovery): Use this only if you cannot access the UMS Server from the UMS Console or the UMS Web App. This function deactivates the certificate chain that was previously used for communication over the Web Port (i.e. the port used for HTTPS; default: 8443; for more information, see IGEL UMS Communication Ports). Also, it creates a new certificate chain which is then used for HTTPS.
If you want to use your own certificate or certificate chain after the reset, see How to Use Your Own Certificates for Communication over the Web Port (Default: 8443) in IGEL UMS.
