Certificate Requirements and Recommendations for the IGEL Cloud Gateway (ICG)
For a successful deployment of the IGEL Cloud Gateway (ICG), a certificate chain for communication with the devices must be provided. This certificate chain must meet a few requirements.
Recommendation: Validity Period of the Root Certificate
The validity period of the root certificate should be as long as possible. When the root certificate expires, all certificates must be exchanged, and all devices must be registered again.
Requirement: BasicConstraint for CA Certificates
The root CA certificate and every intermediate CA certificate must be marked as CA certificate as defined in X509v3 extensions: 2.5.29.19. This is the case if the BasicConstraint extension "is_ca" is set to "true". If it is set to "false", the certificate can not be used for signing other certificates.
Requirement: If a CA Counter Exists, It Must Be Set Correctly
Some CA certificates have a CA counter, defined in X509v3 extensions: 2.5.29.19. The CA counter describes how many members can be added to the certificate chain. If, for instance, the CA counter of the current certificate is 1, it is possible to sign a certificate with which one further certificate can be signed. The CA counter of this certificate is 0, so it can only sign end certificates.
With UMS 6.02 or higher, you can review the CA counter of a certificate by selecting the context menu and then selecting Show certificate content.
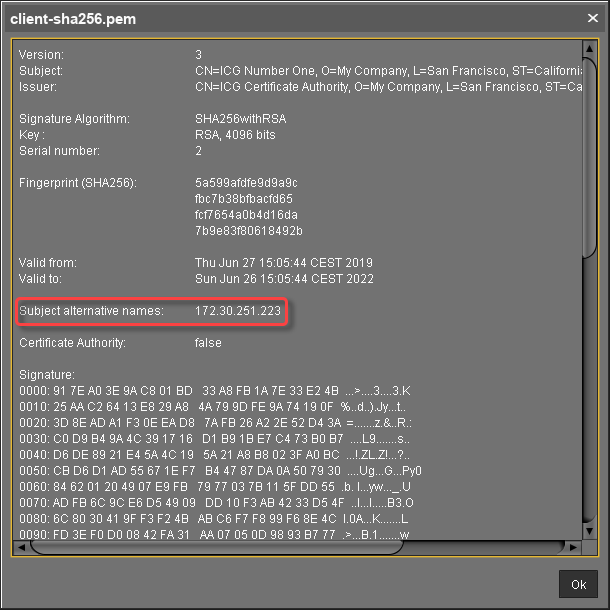
Requirement: End Certificate Must Be Marked and Provide Correct Subject Alternative Name
The certificate to be installed on the IGEL Cloud Gateway must be marked as the end certificate.
The end certificate must have a Subject Alternative Name (X509v3 extensions 2.5.29.17) that contains all hostnames or IP addresses via which the UMS and the devices will contact the IGEL Cloud Gateway. Wildcards are supported.
With UMS 6.02 or higher, you can check this by selecting the context menu and then selecting Show certificate content. The certificate content view should look similar to this: