Introduction
Two methods of single sign-on for a session are available:
Kerberos Passthrough | Real Kerberos authentication with clients that support Kerberos. Within a session, you can access network resources, e.g. file servers, without having to authenticate yourself again; this works automatically via Kerberos. |
Passthrough | Uses cached credentials (user name and password) from local log-on for authentication. For access to network resources within sessions, you have to enter your credentials again. |
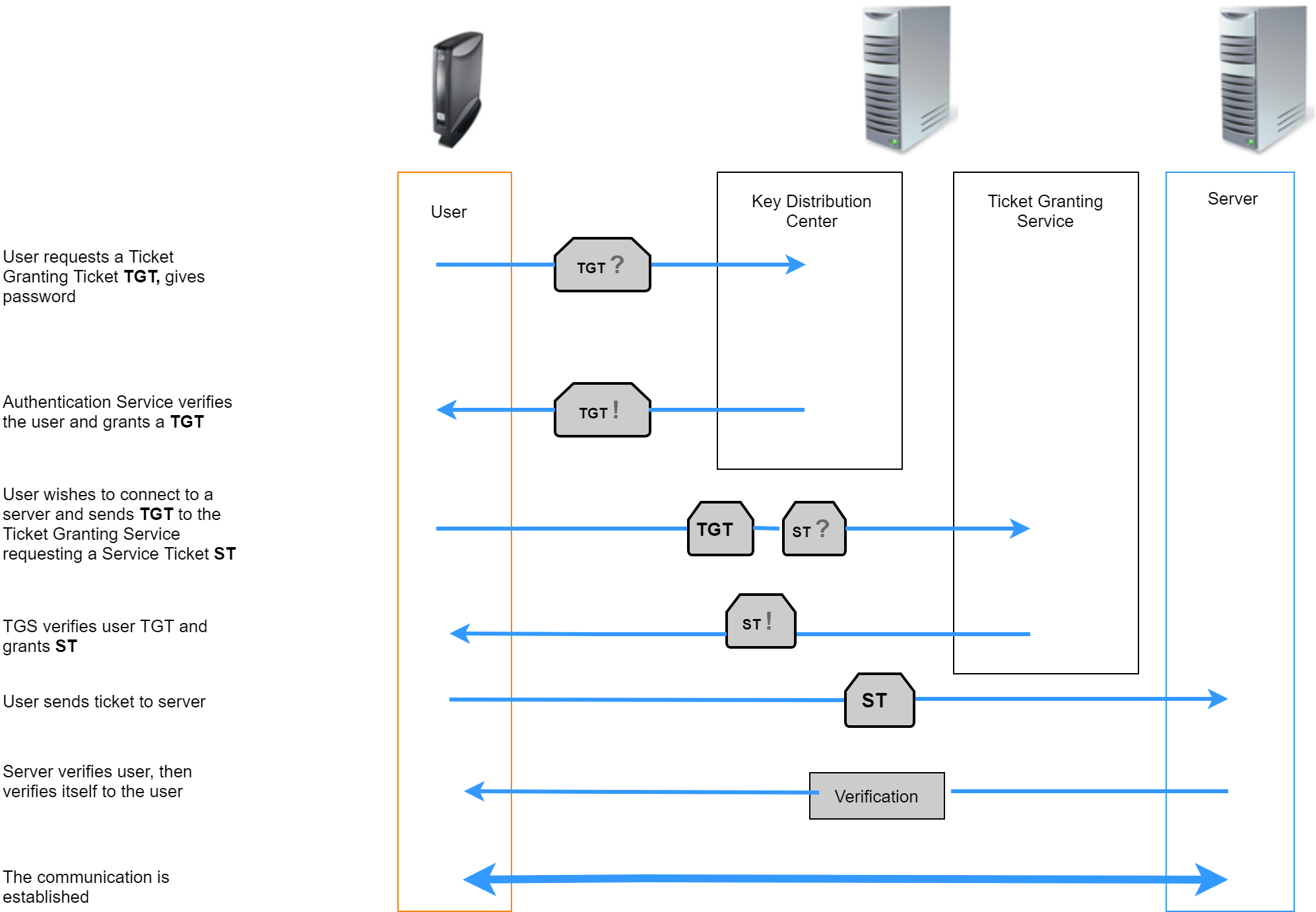
Kerberos is an authentication service. It operates with user, service and computer entities which are known as principals. These principals all belong to a realm, an administrative unit. Each principal has a unique principal name within the realm. To provide the authentication system, a service known as key distribution center is used.
As an example, Microsoft Windows Domains form a realm. The Windows Domain name is the realm name (in upper case letters), e.g. EXAMPLE.COM. A user principal would be for example user@EXAMPLE.COM. The domain controllers take on the role of the key distribution centers.
When logging in, a user obtains a ticket granting ticket from the key distribution center. This ticket expires after a certain time (usually 1 day). When the user starts an ICA session for example, the client can obtain a so-called service ticket from the key distribution center with the aid of the ticket granting ticket. With this service ticket, authentication for the ICA server is accomplished.
To enable passthrough authentication you have to make certain settings: