Shadow Devices Securely
In order to shadow a device securely (with encryption), the administrator must log on to the server via the UMS console. When doing so, it is irrelevant whether a purely local UMS administrator account is used or the user was adopted via an Active Directory for example. As always, however, the UMS administrator must have the permission to shadow the object, see Object-Related Access Rights under Archive > UMS 6 PDF.
The device to be shadowed is called up in the structure tree and, as usual, can be executed via Shadow in the context menu. The connection window, however, differs from the dialog for normal VNC shadowing. The IP and port of the client to be shadowed cannot be changed, and a password for the connection is not requested – this is superfluous after logging on to the console beforehand.
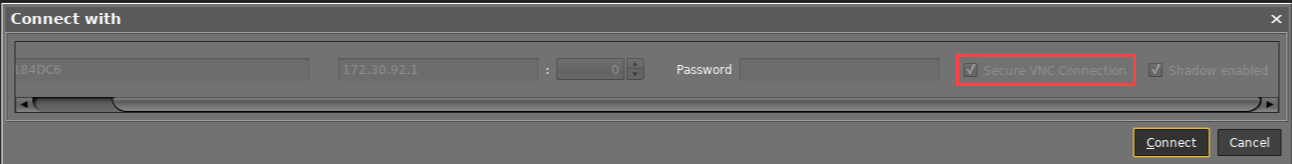
When a VNC connection has been established, the symbol in the connection tab indicates secure shadowing: