VNC Logging
Connections via secure shadowing are always logged in the UMS. Via UMS Administration > Global Configuration > Remote Access > Secure VNC, you can configure whether the user name of the person shadowing is to be recorded in the log:
Log user for secure VNC
☑
The user name is included in the log.☐
The user name is not included in the log. (default)
The VNC log can be called up via the context menu of a device or folder (for several devices, Logging > Logging: Secure Access Logs). The name, MAC address and IP address of the shadowed device, the time and duration of the procedure and, if configured accordingly, the user name of the shadowing UMS administrator are logged.
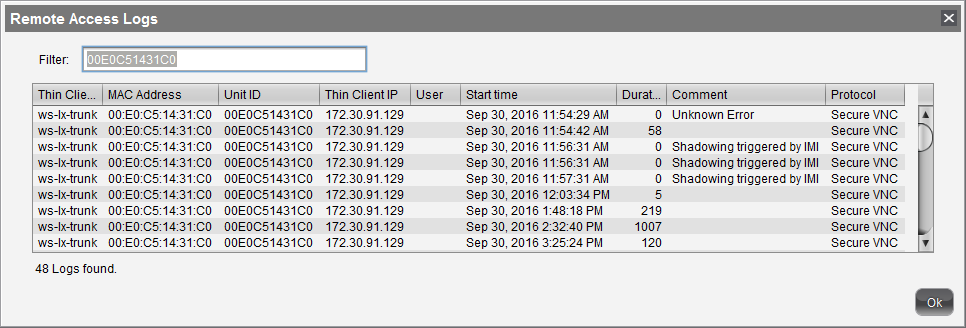
->To sort the list (e.g. according to user names), click on the relevant column header or filter the content shown by making entries in the Filter field.
