Technical Background
The Simple Certificate Enrollment Protocol (SCEP) defines a way of automatically enrolling certificates for the authentication of network devices or VPNs. The client uses HTTP requests to fetch root certificates, to send certificate requests, and to fetch client certificates from the server.
For an in-deep description, see the Microsoft technet article "Network Device Enrollment Service (NDES) in Active Directory Certificate Services (AD CS)" under http://aka.ms/ndes.
Here is a typical certificate enrollment process:
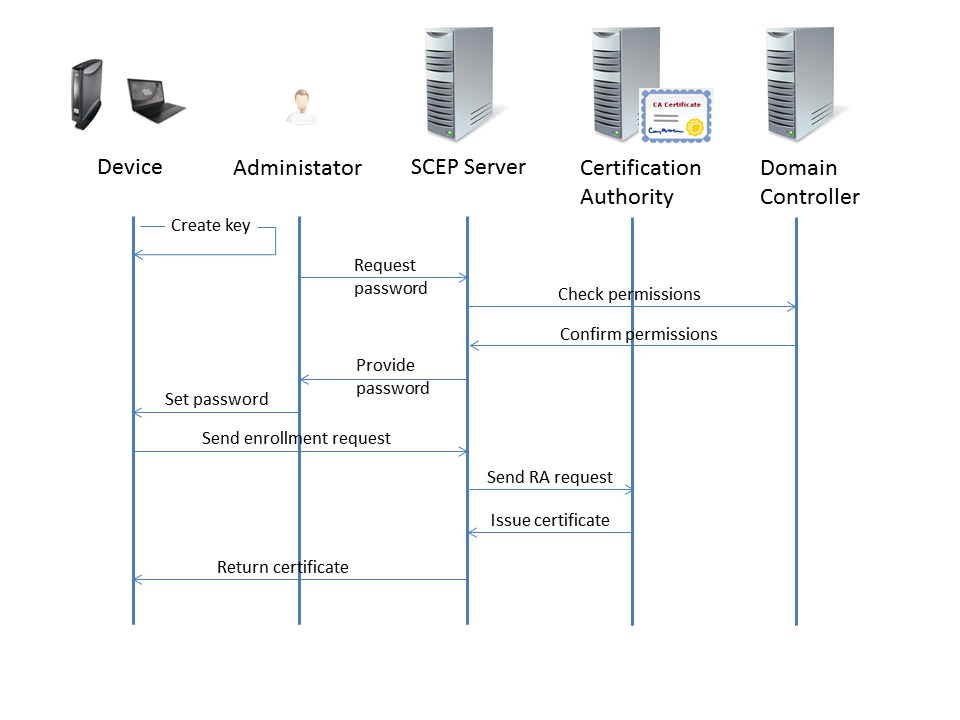
The device creates an RSA public-private key pair.
The administrator requests a challenge password from the SCEP service (e. g. NDES).
The challenge password is only required for the first enrollment request. For certificate renewal, the current certificate is used for authentication.The SCEP server asks the domain controller if the administrator holds the required permissions for the configured certificate templates.
The domain controller confirms that the administrator holds the required permissions.
The SCEP server creates a challenge password and hands it over to the administrator.
Typically, the challenge password expires after a defined time. With the NDES that is included in Windows 2008 Server, the default expiry time is 60 minutes.The administrator provides the device with the challenge password, the CA identifier, and the fingerprint of the CA certificate.
The device sends the enrollment request to the SCEP server, using the challenge password to authenticate with the SCEP server. This action is triggered by the administrator.
The SCEP server signs the enrollment request with its enrollment agent certificate and sends it to the CA.
The CA issues the desired certificate and returns it to the SCEP server.
The SCEP server returns the certificate to the device.
