Device Encryption in IGEL OS 12
If you want to strengthen the security of your endpoint device, you can deploy strong device encryption that is derived from a user password. The encryption is applied to all partitions that can contain user data, e.g. browser history or Custom Partitions.
Menu path: Security > Device Encryption
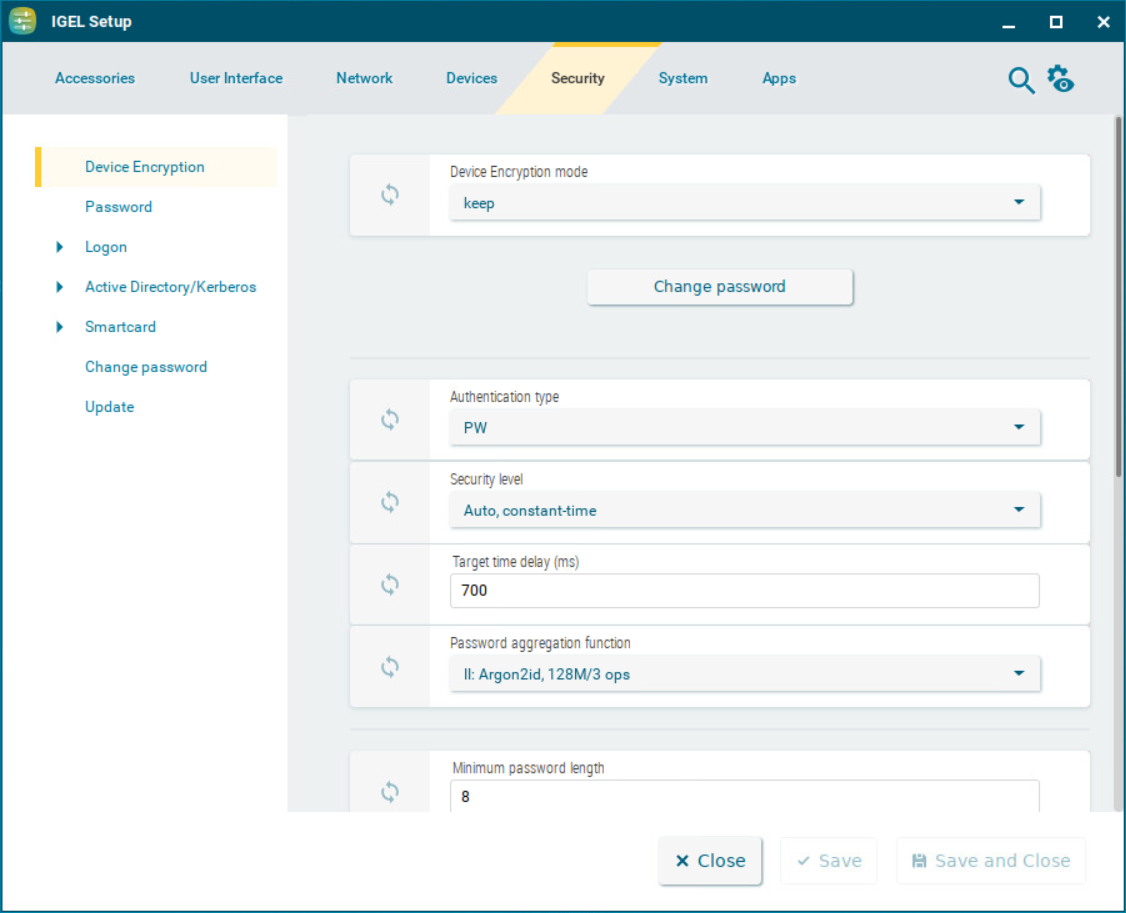
Device encryption mode
Possible options:
Keep: The default encryption scheme is maintained. If a password has been set, it will remain unchanged. (Default)
Activate: The device will be re-encrypted using strong encryption methods when the user enters the password for the first time. It is strongly recommended to enforce the use of a strong password; see Minimum password length and the subsequent password settings. The re-encryption may take about 10 to 60 seconds; the duration depends on the hardware performance and the size of the Custom Partition.
Deactivate: The device will be re-encrypted back to the default device encryption scheme on the next boot. The re-encryption may take about 10 to 60 seconds.
If you want to switch back to the default device encryption, you must have the password. If the password gets lost, you must reinstall IGEL OS on the device, for example, using the OS Creator. For detailed instruction, see How to Start with IGEL > Installing the Base System via IGEL OS Creator (OSC).
Change password
Only applicable if device encryption is activated. Click the button to change the password for device encryption.
Authentication type
Devices That Support TPM PCR
TPM PCR is only supported by the following devices:
HP T640
IGEL UD 3 (M350C with Bios version V:3.D.13A-05232022 or higher)
IGEL UD 7 (H860C with Bios version 3.6.13A-05202022 or higher)
If TPM PCR is selected on a device that does not support it, the authentication type falls back to PW (password authentication).
If TPM PCR+PIN is selected on a device that does not support it, the authentication type falls back to TPM+PIN.
Possible options:
PW: Password authentication.
TPM+PIN
TPM PCR
TPM PCR+PIN
Security level
Possible options:
Auto, constant-time: The password aggregation function that fits best with the defined Target time delay (ms) is selected and the manual selection under Password aggregation function is ignored. (Default)
Auto, at least level: The security level will be at least as high as the value selected by Password aggregation function; if the Target time delay (ms) allows for a higher security level, the higher security level will be used.
Manual: The Password aggregation function can be set manually, irrespective of the delay time specified by Target time delay (ms).
Target time delay (ms)
Maximum time that should be consumed by the password aggregation function. This delay is effective when the user enters the device encryption password on boot or changes the device encryption password. (Default: 700)
Password aggregation function
Security level of the encryption.
Possible options:
I: Argon2id, 8M/7 ops
II: Argon2id, 128M/3 ops (Default)
III: Argon2id, 256M/3 ops
IV: Argon2id, 512M/3 ops
V: Argon2id, 1024M/4 ops
VI: Argon2id, 128M/4 ops
Minimum password length
Minimum number of characters the password must be composed of. (Default: 8)
Unwanted strings in password (comma separated)
Comma-separated list of strings that must not be in the password
The password must contain
Defines how many of the subsequent minimum requirements (minimum amount of lower case letters, etc.) must be fulfilled.
Possible options:
All (Default)
2 of
3 of
Minimum amount of lower case letters
Defines at least how many lower case letters must be in the password.
Minimum amount of upper case letters
Defines at least how many upper case letters must be in the password.
Minimum amount of numbers
Defines at least how many numbers must be in the password.
Minimum amount of special characters
Defines at least how many special characters must be in the password.
Special characters allowed
Lists all the non-alphanumerical characters without separators that are allowed in the password.
