Configuration of an AWS Application Loadbalancer (ALB) for Deploying the IGEL Universal Management Suite (UMS)
This article provides instructions for configuring an AWS Application Load Balancer (ALB) with mTLS support to prepare for installing an IGEL Universal Management Suite (UMS) Server on an Amazon Elastic Compute Cloud (EC2) instance.
We set up an Application Load Balancer (ALB) in AWS to securely expose the UMS Server application, running on port 8443, with HTTPS and mTLS enabled. The ALB uses a trust store stored in S3 and forwards requests to a registered EC2 instance. To support client certificates forwarded from the ALB, the UMS Server must be configured to support Base64 decoding by setting the encodingType to URL_AWS.
Component | Value |
|---|---|
ALB Type | Application Load Balancer |
Scheme | Internet-facing |
Listener Port | HTTPS 8443 & 443 |
Target | EC2 Instance running UMS |
mTLS | Enabled (on port 8443) |
Trust Store | Client Certificate Chain in S3 bucket |
Encoding |
|
AWS Configuration
Setting up an EC2 Instance
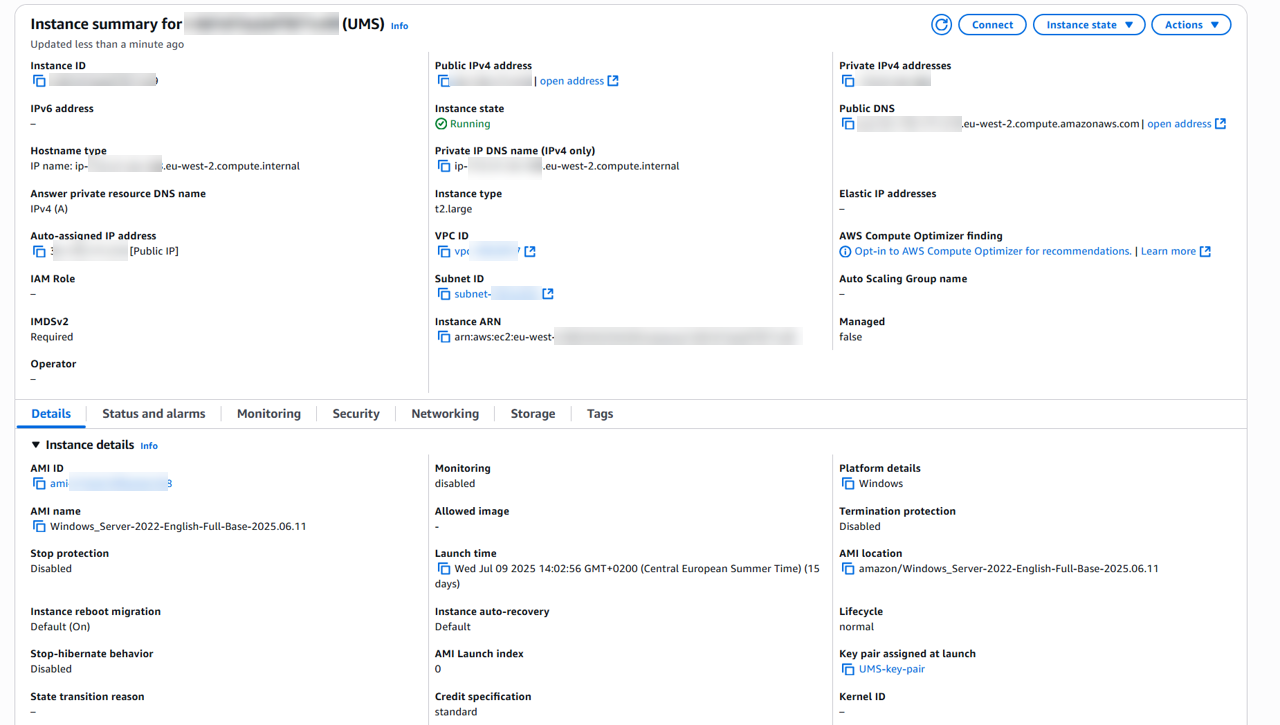
Launch a new EC2 instance using the Windows Server 2022 AMI with the following settings:
Ensure the instance has a security group allowing HTTPS (8443) inbound traffic from the ALB's security group.
Assign a static public IP address
Creating a Target Group
Create a new Target Group, e.g. with “UMS-TargetGroup“ as the name, with the following settings:
Target type:
InstanceProtocol : Port:
HTTPS : 8443Health check path:
UMS:
/infoICG:
/usg/check-status
Success codes:
200


Exporting the CA Certificate Chain from the UMS
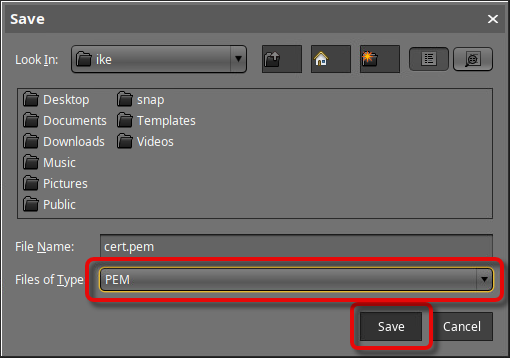
→ In the UMS Console, go to UMS Administration > Global Configuration > Server Network Settings > Export Client Certificate Chain, click Export, and save the certificate file in PEM format to a suitable location.

Creating a Trust Store with the UMS CA Certificate Chain via S3
→ Create an S3 bucket and upload the CA certificate chain you have just created.
Exporting the UMS Web Certificate Chain
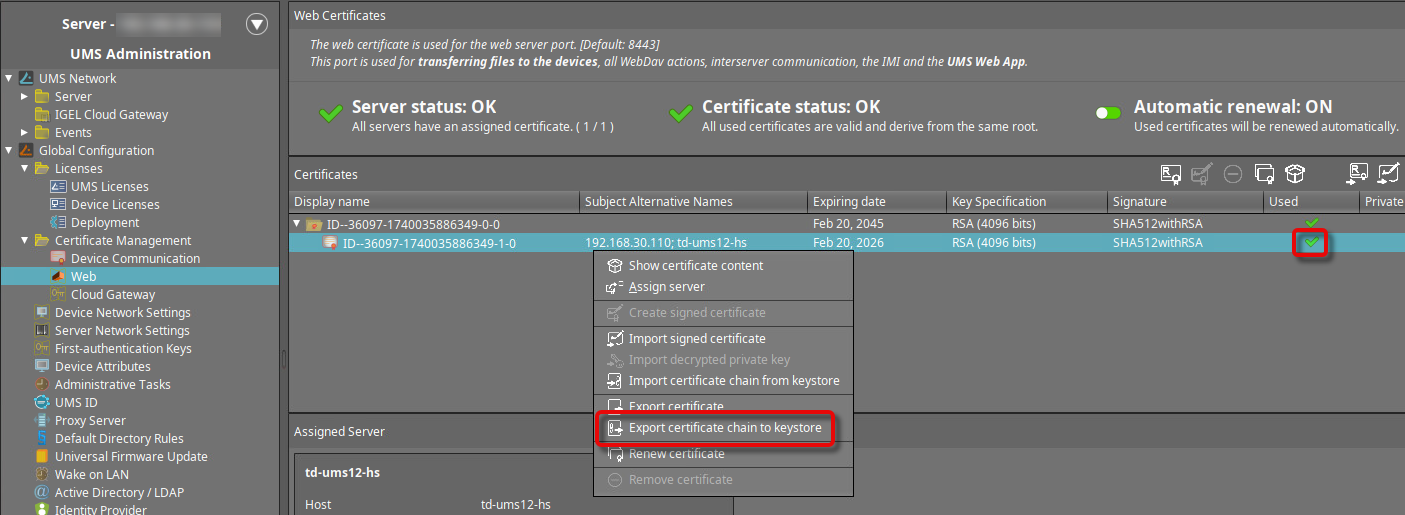
Select the web certificate that is currently in use, open the context menu, and click Export certificate chain to keystore.
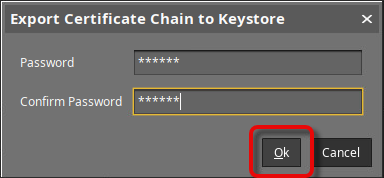
Set a password for the keystore.
Save the keystore file to a suitable location.
Open the keystore file with a suitable tool, e.g., KeyStore Explorer.
Enter the password you have defined during the export from the UMS.
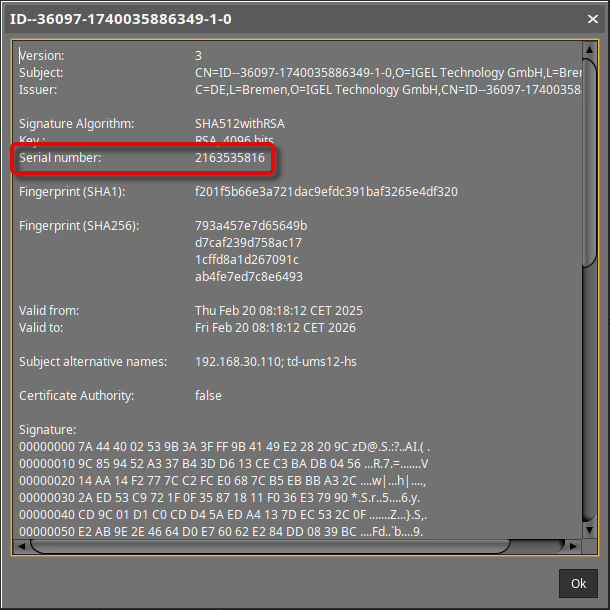
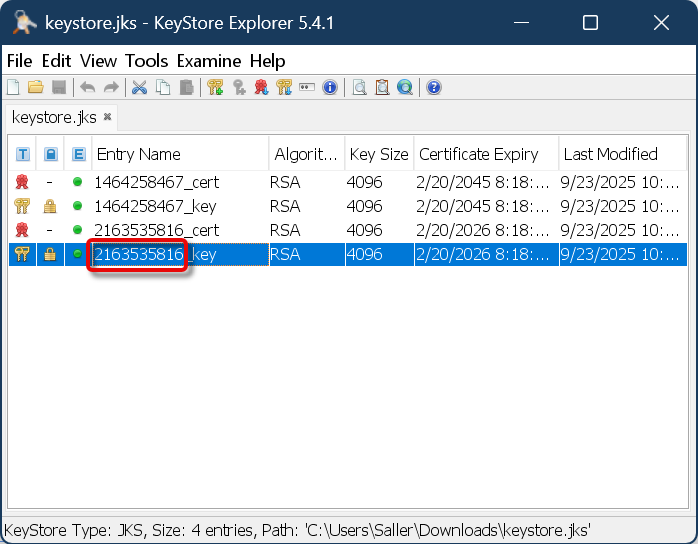
Select the correct key pair by comparing the entry name in the keystore tool with the serial number displayed in the UMS when you click Show certificate content.

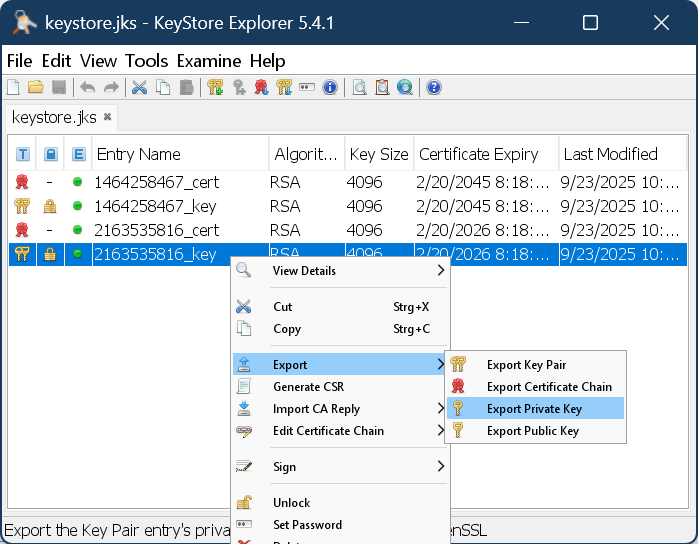
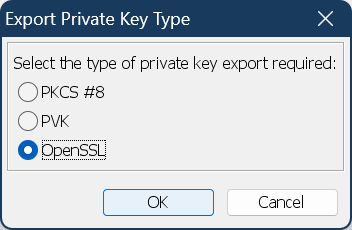
Export the private key with the following properties:
Type: OpenSSL
Unencrypted
PEM is activated
Appropriate filename, e.g., something with “private_key”

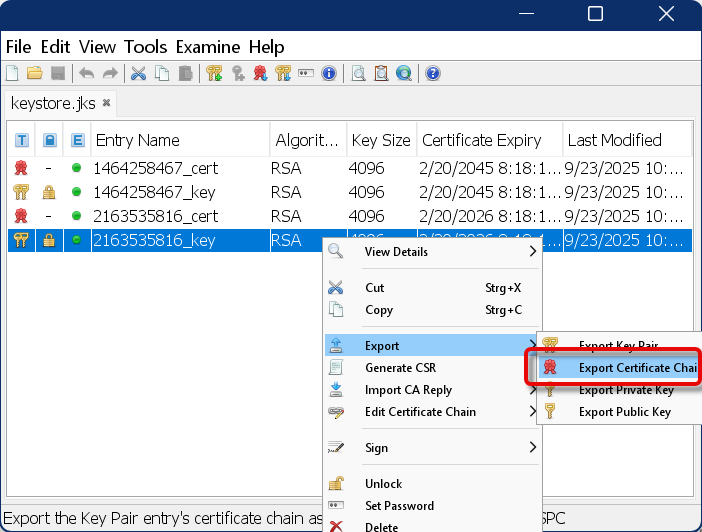
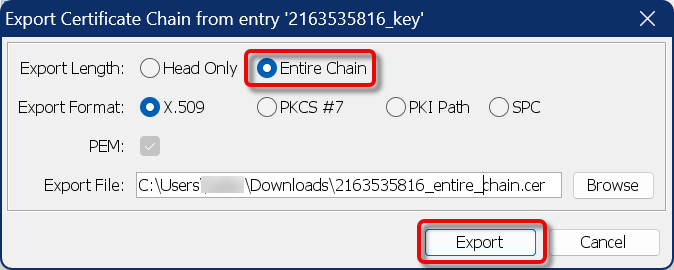
Export the certificate chain with the following properties:
Export length: Entire chain
PEM is activated
Appropriate filename, e.g., something with “entire_chain”
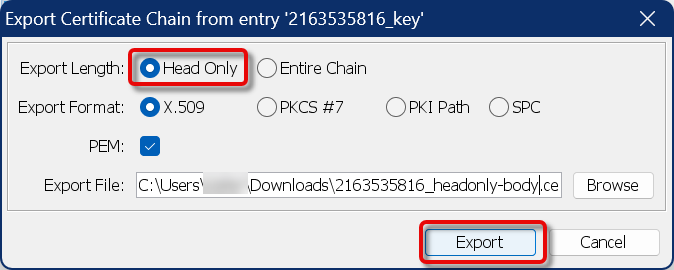
Export the certificate chain, this time with the following properties:
Export length: Head only
PEM is activated
Appropriate filename, e.g., something with “headonly-body”

Configuring the ALB Listeners
In the following, we will create an ALB with two listeners
Create an Internet-facing ALB.
Create a listener that listens for HTTPS connections with mTLS on port 8443 and forwards traffic to the UMS target group.
Click Import a certificate and paste the complete contents of the files we have exported from the keystore:
Certificate private key: Paste the content of the file we created in Exporting the UMS Web Certificate Chain, step 7.
Certificate chain (optional): Paste the content of the file we created in Exporting the UMS Web Certificate Chain, step 8.
Certificate body: Paste the content of the file we created in Exporting the UMS Web Certificate Chain, step 9.

Once imported, the certificate becomes available in the AWS Certificate Manager (ACM).
Under mTLS settings, enable Verify with Trust Store and link to the S3 bucket with the UMS CA certificate chain you have created beforehand.

Create another listener that listens for HTTPS connections with standard TLS (no mTLS) on port 443 and forwards traffic to the UMS target group.
Click Import a certificate and provide the same certificate configuration as you did for the first listener in step 4.
Configuring Logging and Monitoring
Enable Access Logs and Connection Logs for the ALB.
Set the log destination to the S3 bucket that is used for the trust store or another one as needed.
Configuring the UMS Server
Adjusting the Server Network Settings
The FQDN of the UMS cluster must be set as the external address. This FQDN of the UMS cluster must be included in your web certificate, and the corresponding certificate must be assigned to all UMS servers:
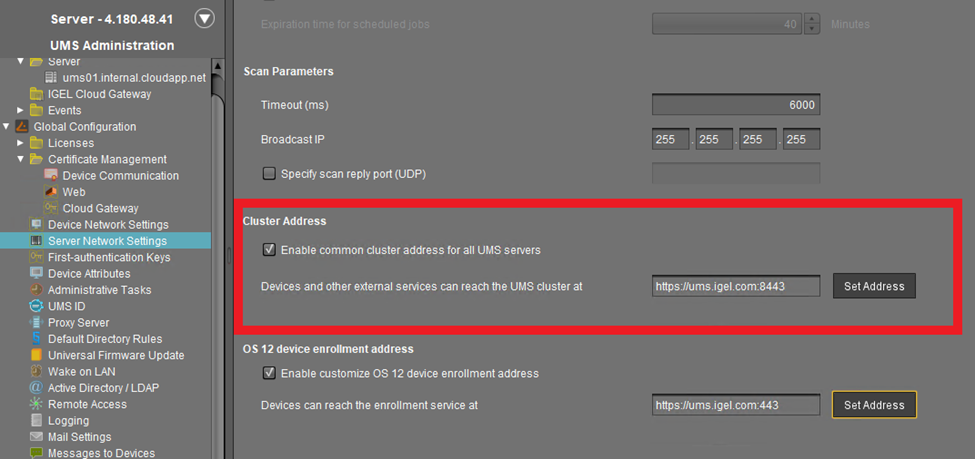
Go to UMS Administration > Global Configuration > Server Network Settings.
Set the Cluster Address to the external address of your AWS ALB.
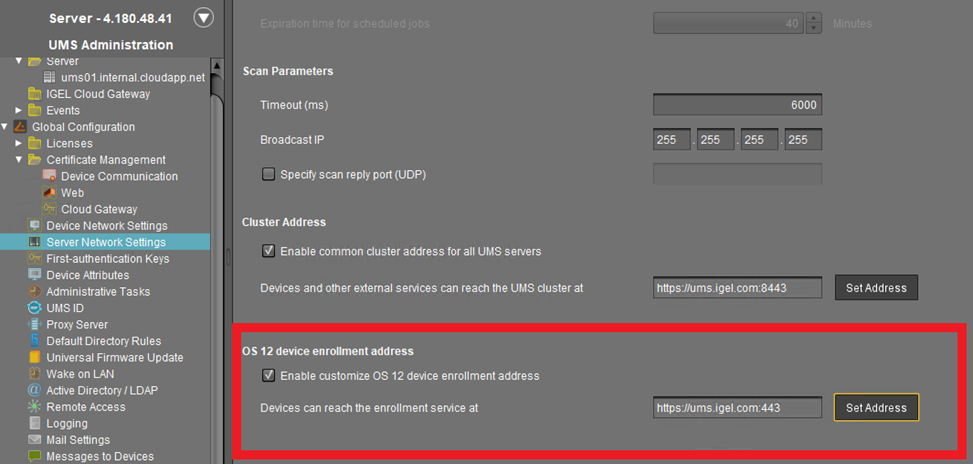
Set the OS 12 device enrollment address to the external address of your AWS ALB.
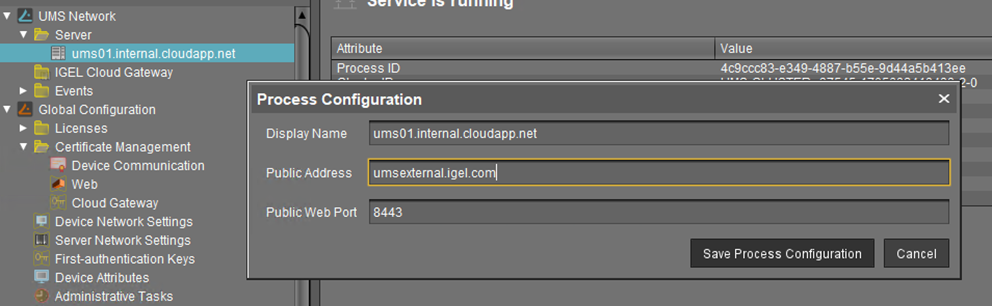
Set Public Address and Port of the UMS Process Configuration
If the public address of the UMS differs from the UMS address, the public address and port must be set. This option can be set under UMS Administration > UMS Network > Server. This is essential for device shadowing.
Create UMS Web Certificate / Cloud Gateway Ce
Setting the UMS Server to Accept the Certificate from the AWS ALB
The AWS ALB sends a header (X-Amzn-Mtls-Clientcert-Leaf) that contains only the client certificate, not the full certificate chain. Therefore, the UMS Server must be configured accordingly.
Edit the file
<UMS installation path>\rmguiserver\conf\appconfig\application.ymlaccording to the example below:
igel:
client-cert-forwarding:
enabled: true
encodingType: URL_AWS
client-cert-forwarded-header: X-Amzn-Mtls-Clientcert-LeafThe encodingType must be explicitly set to URL_AWS to properly decode the certificate format used by the ALB, which URL-encodes the PEM-formatted certificate.
Restart the UMS Server.
