Options for OpenVPN Client-Server Communication on IGEL OS
Here, you can configure the interaction between the OpenVPN client on IGEL OS and the server.
Further information regarding the options can be found in the OpenVPN documentation which is maintained by the OpenVPN project.
Menu path: Setup > Network > VPN > OpenVPN > [OpenVPN Connection] > Options
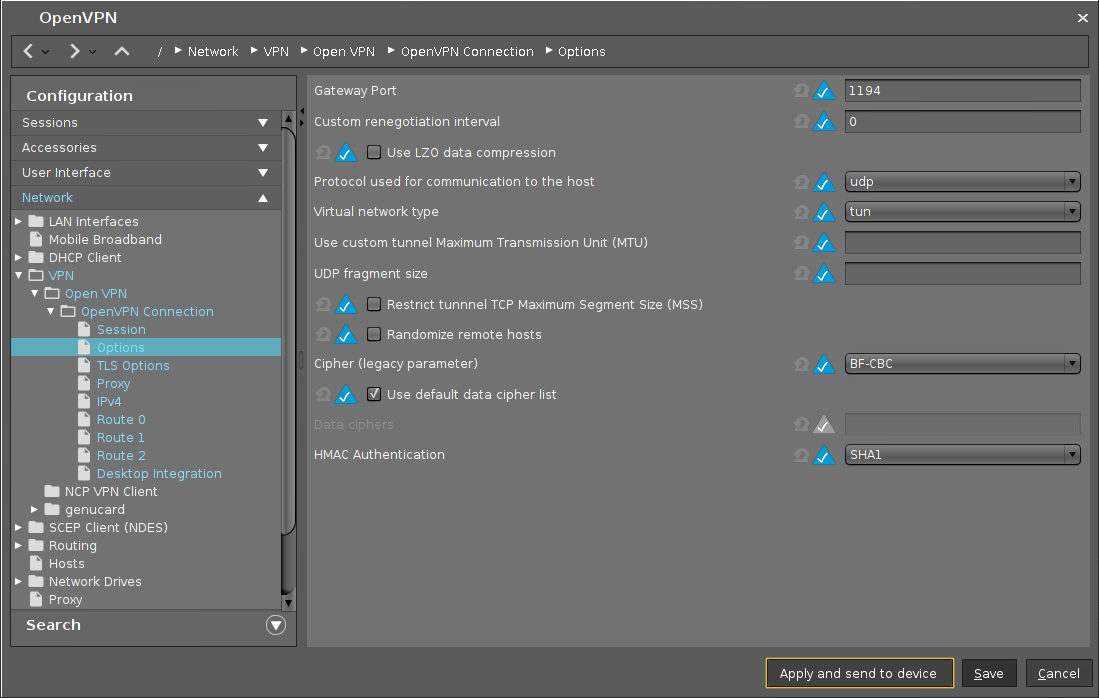
Gateway Port
Local gateway port. Default: 1194
Custom renegotiation interval
Renegotiate data channel key after a given number of seconds. (Default: 0)
Use LZO data compression
From OpenVPN v2.4, LZO data compression ("comp-lzo") is deprecated.
☑ The client will use LZO compression. Necessary if the server uses compression.
☐ The client will not use LZO compression. (Default)
Protocol used for communication to the host
- udp: UDP will be used. (Default)
- tcp-client: TCP will be used.
Virtual network type
- tun: Routing will be used. (Default)
- tap: Bridging will be used.
Use custom tunnel maximum transmission unit (MTU)
The MTU of the TUN device will be used as a given value. The MTU of the interface will be derived from it.
UDP fragment size
Allow internal data fragmenting up to this size in bytes. Leave this field empty to keep the default value.
Restrict tunnel TCP maximum segment size (MSS)
☑ The TCP segment size (MSS) of the tunnel will be restricted.
☐ The TCP segment size (MSS) will not be restricted. (Default)
Randomize remote hosts
☑ The remote gateways will be ordered randomly as a simple type of load balancing.
☐ The remote computers will not be ordered randomly. (Default)
Cipher (legacy parameter)
Encryption algorithm for data packets. If you do not want to use any of the ciphers in this menu, select unset. Default: BF-CBC (Blowfish in the Cipher Block Chaining mode)
Use default data cipher list
The default list of ciphers that are to be negotiated between client and server is "AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305".
☑ The default cipher list is used. (Default)
☐ The list provided in Data ciphers is used.
Data ciphers
You can enter enter a custom list of ciphers. The ciphers must be separated by a semicolon ';'. Example: "AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305"
HMAC authentication: Hashing algorithm for packet authentication (default: SHA1)
