Download PDF
Download page Logging and Log Evaluation.
Logging and Log Evaluation
Prerequisites
Teleworking computers should have a logging function and should have a log evaluation function.
Note
IGEL recommends leaving logging enabled by default (authentication, kernel, and daemons) and limiting the desired parameters by filtering during evaluation.
Action: Forward Logs to Log Analyzer
Use a log collector and analyzer, which allows the archiving and analysis of logs according to many aspects, such as Graylog, Splunk or the Elastic-Logstash-Kibana-Stack (ELK). Their evaluation function must be able to differentiate according to the types of data required for logging (for example, filtering all unauthorized access to all resources in a given period of time). The evaluation function must generate evaluable (readable) reports so that no security-critical activities are overlooked.
Such solutions can receive log data via rsyslog interface with TLS encryption. In IGEL OS, configure the forwarding as follows:
Installing the Certificate
If the X.509 certificate of your log collector is not signed by a CA known to IGEL OS, install the CA root certificate of the signer as follows:
- Create a new file in the UMS Console under Files by right-clicking.
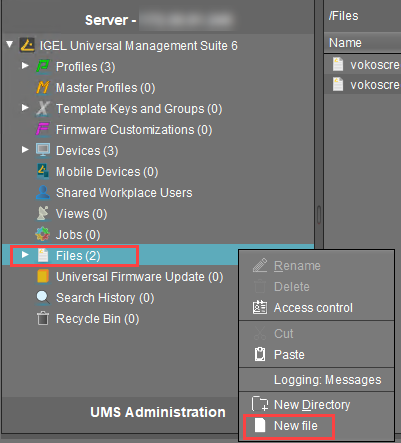
- Under Local file, select the CA root certificate file
ca.pemin PEM format and upload it. - Under Classification, select "Undefined".
- Enter
/wfs/ca-certs/for the Device file location. - Enable read and write permission for the Owner, read permission for Others and set the Owner to Root.
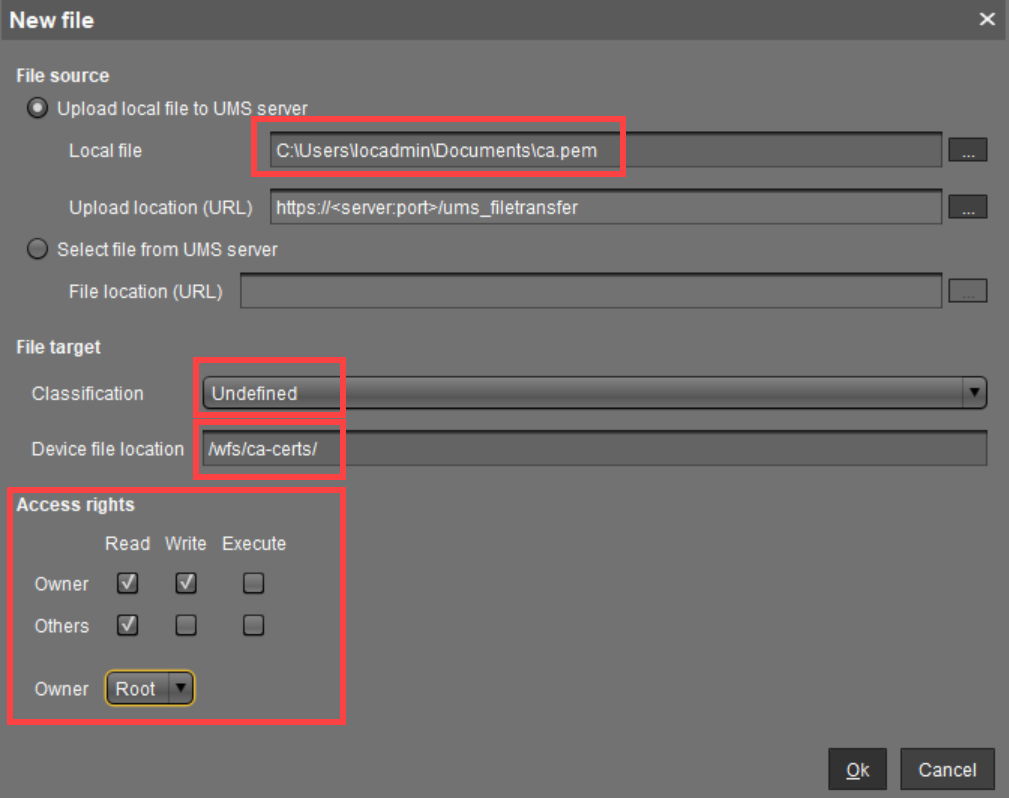
- Click Ok.
- Assign the file object to the desired devices.
Configuration of Log Forwarding on IGEL OS
As of IGEL OS 11.06.100, you can configure the log forwarding with TLS encryption as follows:
- In the UMS, create a new profile. See Creating Profiles.
- In the configuration dialog, go to System > Logging.
- Set Remote mode to "Client".
- Click the Add button.
- Make the required settings and activate TLS enabled.
- Under CA certificate, specify the path to the CA root certificate you have installed previously, e.g.
/wfs/ca-certs/ca.pem.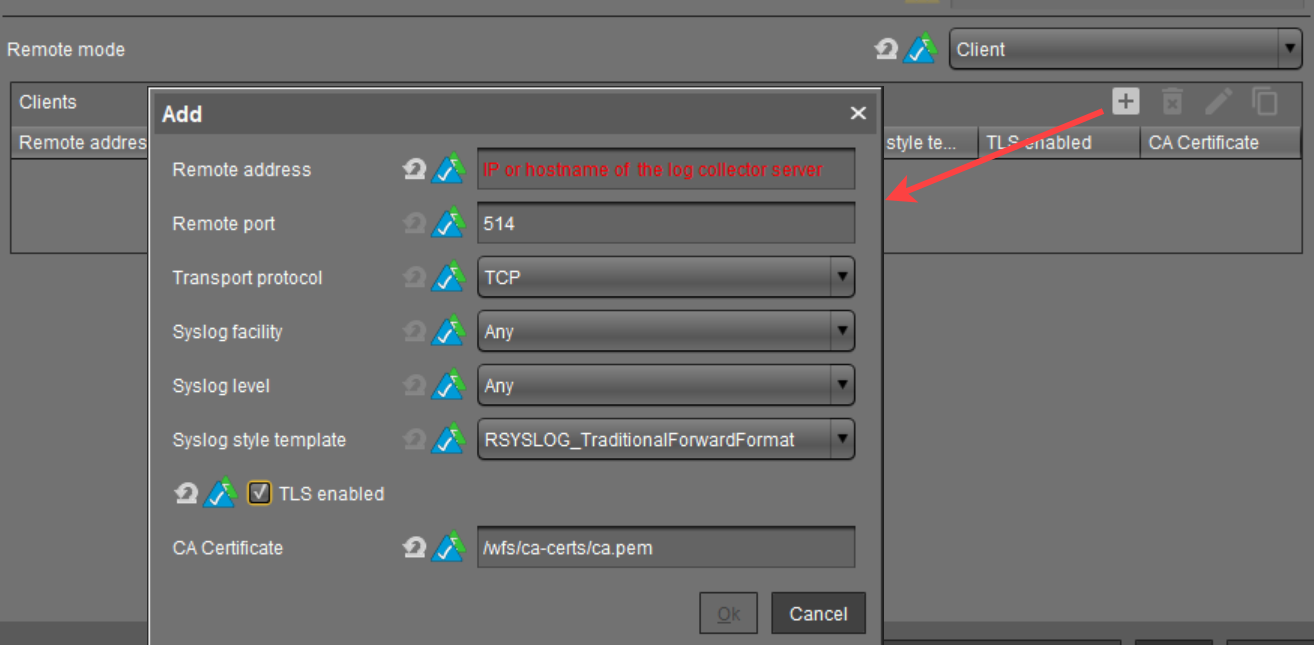
- Save the changes and assign the profile to the desired devices.
- Reboot the devices to make the change effective.
In IGEL OS before version 11.06.100, configure the log forwarding with TLS encryption as follows:
- Create a text file
50-tlslog.confwith the following content:global(DefaultNetstreamDriverCAFile="/wfs/ca-certs/ca.pem")*.* action(type="omfwd" protocol="tcp"Target="<IP address or DNS name of the log collector>" port="<Port of the log collector)"StreamDriver="gtls" StreamDriverMode="1" StreamDriverAuthMode="anon"template="RSYSLOG_TraditionalFileFormat") - Create a new file in the UMS Console under Files by right-clicking.
- Under Local file, select the file
50-tlslog.confand upload it. - Under Classification, select "Undefined".
- Enter
/wfs/under Device file location. - Enable read permission for the Owner and for Others and set the Owner to User.
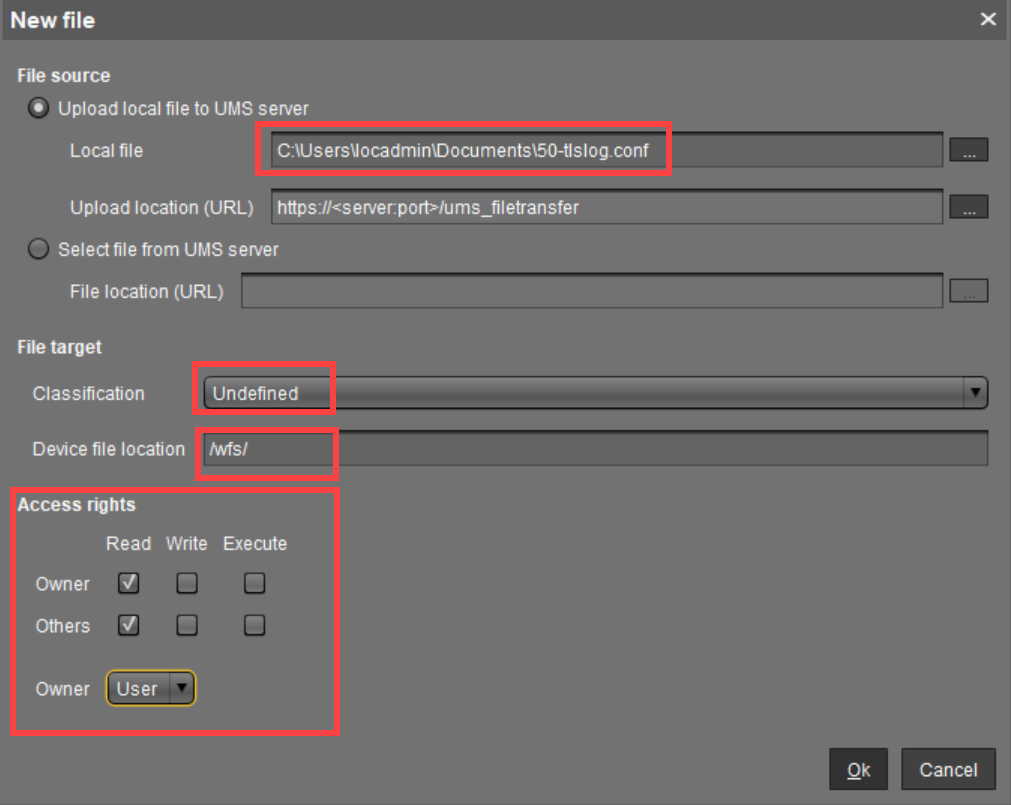
- Click Ok.
- Assign the file object to the desired devices.
- Create a profile with the following content:
- In the configuration dialog, go to System > Firmware Customization > Custom Commands > Basic.
- Enter the following line in the Initialization field:
cp /wfs/50-tlslog.conf /etc/rsyslog.d/
- Assign the profile to the desired devices.
- Reboot the devices to make the change effective.
Action: Analyze Configuration Changes
In addition, various log entries for administrative activities can be searched in the Universal Management Suite:
- Choose System > Logging > Log Messages to see when settings and commands were sent to which device.
- Choose System > Logging > Event Messages to see changes to objects in the Universal Management Suite.
- Choose System > Logging > Remote Access to find out when which UMS user has shadowed which device using Secure Shadowing.