UMS Login Requirements
With UMS 12.08.100, the login process has changed, which entails new requirements for your environments.
Overview
The main benefits of the new login process are:
Increased security
Support of Cloud IdPs, like Microsoft Entra ID, Okta, or PingIdentity
Modernized and centralized login process for the UMS Web App and the UMS Console
For the login process, see Connecting the UMS Console to the IGEL UMS Server.
The UMS login process uses the following protocols:
oAuth2
OpenID Connect
JWT
Browser Requirements
The login procedure requires a modern browser on the system. For a list of supported browsers, see the Supported Environment section of the corresponding Release Notes.
UMS Web Certificate
The UMS Web Certificate must contain all possible address formats that will be used for login in the UMS Console or UMS Web App. The following formats are possible:
FQDN
ShortName (hostname only)
IP address used to connect to the UMS Web App or the UMS Console
Reason: The login process executes a full SSL Handshake and verifies if the certificate presented is issued for the requested FQDN or IP Address.
UMS Server Public Address / Cluster Address
The public address of the UMS Server must be set correctly, in line with the UMS web certificate. For details, see Set the Correct Public Address and Public Web Port for each UMS server.
Reason: The authentication service of the UMS validates the redirect URI provided by the client (UMS Web App or UMS Console) against the registered values. From UMS 12.08.100 onward, the redirect URIs are derived from the UMS Server public address resp. the cluster address.
Logging in to the local machine as the UMS superuser (with “localhost” as the server address) is always possible. This can help fix login issues.
Redirect URIs for UMS Web App Login
If you use a URL to login to your UMS, which is not detected automatically (see above) you can add additional redirect URIs:
Log in to the UMS by logging in to the server itself with localhost.
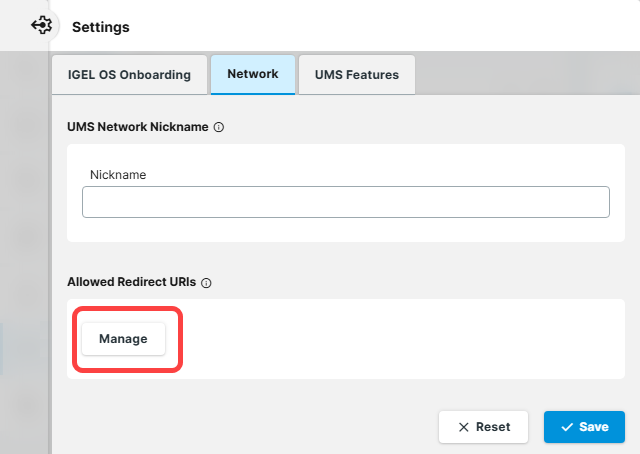
Open the UMS Web App and go to Network > Settings.
Click Manage under Allowed Redirect URIs.
Add additional redirect URIs in the format
https://{host}:{port}
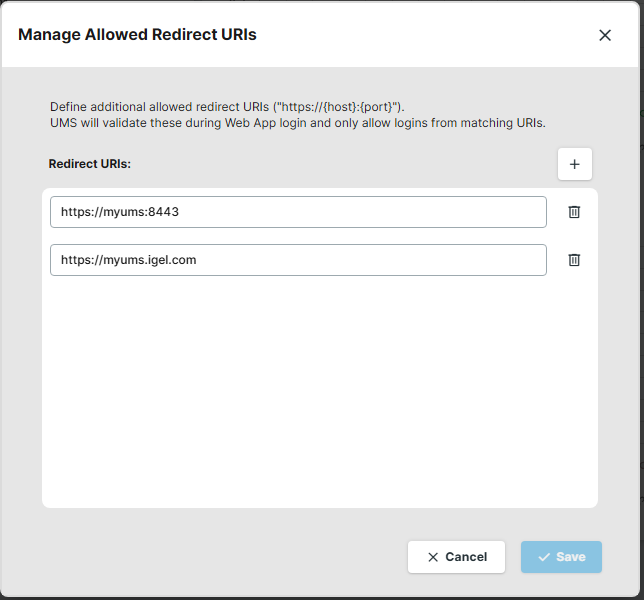
After saving, you will be able to login with these configured URIs.
The redirect URIs configured here must be contained in the UMS Web Certificate.
Active Directory (AD) Users
An AD user must have a configured user name and password in the AD configuration to log in.
Reason: With the previous UMS version, the password of the login user was cached and used for refreshing the user data. Now, for security reasons, a valid AD user is required to refresh the user data. This user must have read access to user account details, group memberships, and other necessary AD data.
Known Issue
In IGEL UMS 12.08.xx versions, AD logon will fail in an environment where the Domain Name System (DNS) cannot map to Key Distribution Centers (KDCs). This mapping is crucial for the UMS to locate the KDC responsible for a specific realm when authenticating.
