Generating and Distributing First-Authentication Keys for Devices
To establish a connection with the ICG, every device must authenticate with the ICG. For this purpose, a first-authentication key must be generated. On first contact with the ICG, the device must present this key.
There are various methods of generating first-authentication keys. The most common one is described here; for alternative methods, see How to Generate First-Authentication Keys for Devices in the ICG.
Creating a New Mass-Deployment Key for Arbitrary Devices
In the UMS Console, go to UMS Administration > Global Configuration > First-authentication Keys.
Click
 .
.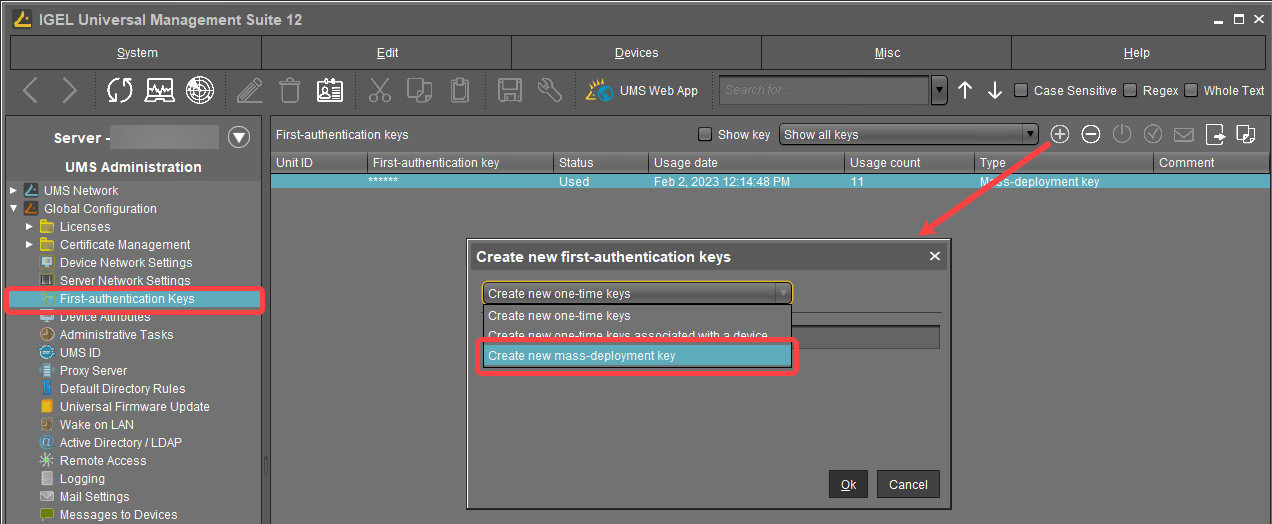
Select Create new mass-deployment key.
Activate or deactivate Generate random mass-deployment key to choose the method of key generation:
 The key is generated by the UMS.
The key is generated by the UMS. You can enter a key of your own in the entry field.
You can enter a key of your own in the entry field.Click OK.
One or more new entries appear in the list.
Distributing the Key via E-Mail or Printed Letter
Go to UMS Administration > Global Configuration > First-authentication Keys.
Select the desired password entries and click
 to copy the credentials to the clipboard.
to copy the credentials to the clipboard.
The data required for connecting a device to the ICG is in the clipboard: host address, ICG server certificate fingerprint, and the password.
The contents of the clipboard will look similar to the following example:----------------------------------------------------------------------------------------------------------------------------Host: 222.222.222.222Port: 8443Root Certificate FingerprintPart 1: 1231231231231231Part 2: 2342342342342342Part 3: 3453453453453453Part 4: 4564564564564564----------------------------------------------------------------------------------------------------------------------------First-authentication key: 17171717171717171--------------------------------------------------------------
The clipboard contains data for all active ICGs. In the example above, 1 ICG connection is active. If, for instance, 3 ICGs were active, the data for those 3 ICGs would be included.To send the credentials via e-mail, paste the data into an encrypted e-mail. To send the credentials in a printed letter, paste the data in your e-mail program or word processor.
